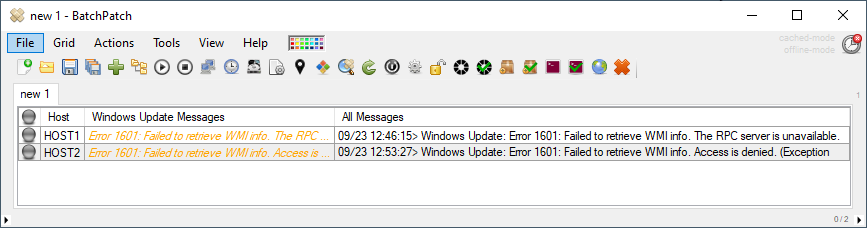
The problem: After installing the June 2022 cumulative Windows Update (2022-06 Cumulative Update for Windows) OR any future cumulative update that is released from this point forward, if the previous patch level of the system was some date prior to June 2022, and the newly installed patch level is June 2022 or newer, you might experience BatchPatch all of a sudden returning an error for no apparent reason: Access is denied. (Exception from HRESULT: 0x80070005 (E_ACCESSDENIED))
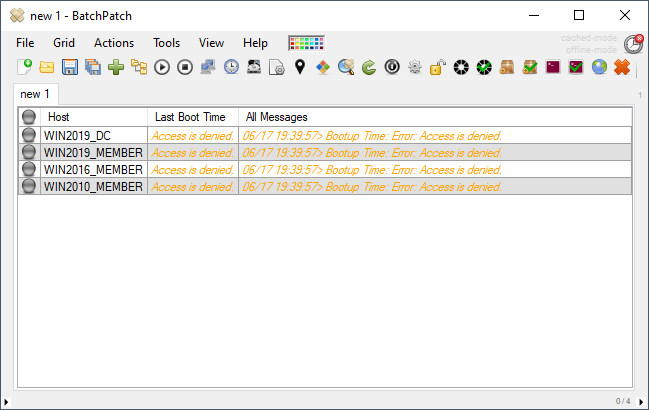
( For general ‘Access is denied’ issues that aren’t specific to the June 2022 cumulative update, please see https://batchpatch.com/troubleshooting-common-errors-in-batchpatch )
Why this is happening: Toward the end of 2021 (the specific date varies depending on the operating system – see below for details) Microsoft released an update that added security hardening to the Distributed Component Object Model (DCOM) remote protocol in Windows to address the security vulnerability CVE-2021-2614. The hardening was available for administrators to enable, but it was not enabled by default… until June 2022 when Microsoft flipped the switch and enabled it for everyone.
The specific dates of release are as follows:
Windows Server 2022 – September 27, 2021
Windows 10, version 2004, Windows 10, version 20H2, Windows 10, version 21H1 – September 1, 2021
Windows 10, version 1909 – August 26, 2021
Windows Server 2019, Windows 10, version 1809 – August 26, 2021
Windows Server 2016, Windows 10, version 1607 – September 14, 2021
Windows Server 2012 R2 and Windows 8.1 – October 12, 2021
Important reading: In the following posting, Microsoft explains the detail of KB5004442, which was released in June 2022. When the Aug/Sept/Oct 2021 update (date depends on OS, as noted above) is installed it makes available a new registry DWORD value HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Ole\AppCompat\RequireIntegrityActivationAuthenticationLevel, which when created and set to value data 1 will enable DCOM security hardening configuration that enables the administrator to test and see what, if anything, it breaks in their environment. In the June 2022 KB5004442 update, the DCOM security hardening configuration was then enabled by default, such that if you did not previously set the aforementioned registry value to 1, Windows would now begin behaving the same as if the value had been set to 1, which could cause some things to break. And now in order to disable the DCOM hardening changes you would have to create and set the value data to 0. Furthermore they note that in March 2023 the DCOM hardening changes will become permanent with no registry value available anymore to disable the configuration.
KB5004442—Manage changes for Windows DCOM Server Security Feature Bypass (CVE-2021-26414)
Temporary workaround: Use the registry value described in the link above (set to value data 0) to disable the DCOM hardening changes temporarily until March 2023. In March 2023 after installing the cumulative update for that month it will be permanently enabled with no further ability to be disabled anymore.
Permanent resolution: BatchPatch will only break and start producing the ‘Access is Denied’ errors described at the top of this posting in the case where the BatchPatch computer is running a Windows operating system at a patch version that is *older* than Nov 2021 AND when at the same time the target computers are running a Windows operating system at a patch version of June 2022 or newer (or if the aforementioned registry value data is intentionally set to 1 by the administrator, then the problem will manifest as soon as the target computer has the Aug/Sept/Oct 2021 update installed).
So, if you began to experience this problem after installing the June 2022 or newer cumulative update on target computers, the simplest resolution is to make sure your BatchPatch computer is updated to the latest Windows cumulative update (or at a bare minimum to a patch level of Aug/Sept/Oct 2021 or newer – The specific date is dependent on the particular version of Windows that you are running. Please refer to the OS version list above as well as the aforementioned link for the specific date for your particular version of Windows).
( For general ‘Access is denied’ issues that aren’t specific to the June 2022 cumulative update, please see Troubleshooting Common Errors in BatchPatch )