Standard Deployment Method for Windows Feature Update 25H2 (and other feature updates/upgrades such as 24H2, 23H2, 22H2, 21H2 etc) in BatchPatch
If Microsoft has already made the update available to your computer, then unless you are using an old version of BatchPatch (released prior to April 2020), you can deploy Windows Feature Update 25H2 using the standard built-in Windows Update actions in BatchPatch under Actions > Windows updates.
However, there are cases where you might want to deploy the update to your computers after Microsoft has published it for public consumption but before it has been designated for deployment to your individual computers (this can happen because Microsoft does not make the update available to every Windows computer on the planet at the same time– they make it available over a period of time). In the case where the update is publicly available but not yet being offered to your computer, you can still deploy it but you’ll need to use the alternate method that’s explained lower down in this tutorial.
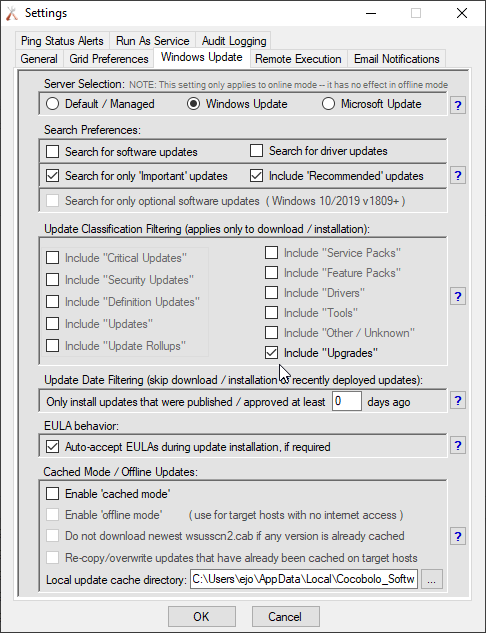
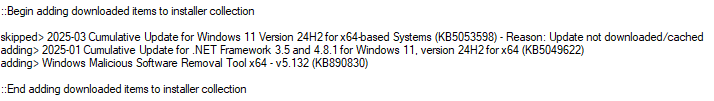
For the typical deployment method, the primary requirement is that the feature update that you wish to install must be offered to the machine and be showing as an available update when you use Actions > Windows updates > Check for available updates in BatchPatch. If you see the 25H2 feature update in that list of available updates for the target computer or group of target computers, then you can just download/install the update on those computers by first modifying the classification filtering in Tools > Settings > Windows Update so that the Include “Upgrades” box is checked.
After the Upgrades classification is selected you can then use Actions > Download available updates in conjunction with Actions > Install downloaded updates or you can just click Actions > Download and install updates. As long as you are operating in standard, non-cached mode in BatchPatch (i.e. cached mode is disabled), feature updates will install (assuming, of course, that you currently have a feature update showing in the list of available updates for a given computer). Note, cached mode is enabled/disabled under Tools > Settings > Windows Update.
Feature Update Deployment Considerations – Update deferral policies, and when an update is only available for “seekers”
Please note there are a couple of things to consider when installing feature updates using the standard non-cached mode BatchPatch update method.
First, as mentioned above, the target computer needs to have the desired feature update showing as one of the available updates for the computer. If you’re expecting to see it but you don’t, it could be because the update is not approved on your WSUS yet, or it could be that you have a Group Policy or Local Policy setting configured for the target computer that is set to defer the installation of feature updates for a specified amount of time. Check your Group Policy configuration for any deferral policies enabled under the following locations:
Computer Configuration > Administrative Templates > Windows Components > Windows Update
Computer Configuration > Administrative Templates > Windows Components > Windows Update > Windows Update for Business
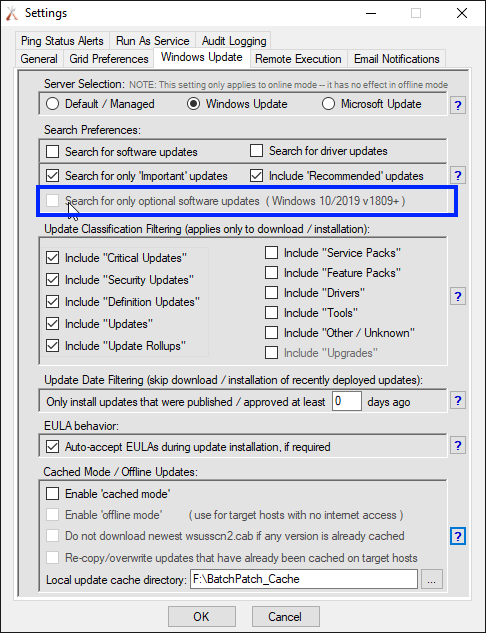
Second, depending at what stage of the rollout Microsoft currently is at the time you attempt to deploy a given feature update, they might not yet be delivering the update through the normal Windows Update channel. They typically begin the rollout with delivery only to “seekers”. This is the name they give to people who manually click on the ‘Check for updates’ button in the Windows Control panel. “Seeker” updates are visible in BatchPatch when you click on ‘Search for only optional software updates‘
Third, over the past couple/few years Microsoft has made quite a few changes to how Windows Update works, particularly with regard to how feature updates are handled. It’s possible that there is some other reason that I didn’t mention above that is the cause for why you are not seeing the feature update available for installation through the normal Windows Update methods.
Alternate Deployment of Windows Feature Update 25H2 (and other feature updates/upgrades such as 24H2, 23H2, 22H2 or 21H2 etc) with BatchPatch (can be used for deployment to offline target computers)
If you need to deploy feature update version 25H2 (or any other feature update) to target computers that don’t have internet access and don’t have WSUS access and therefore cannot be targeted in standard, non-cached mode (that is to say, you are using either online cached mode or offline cached mode with those target computers, and you are not able to disable cached mode and switch to standard mode for whatever reason), then you may use the method outlined below to deploy the feature update to those computers.
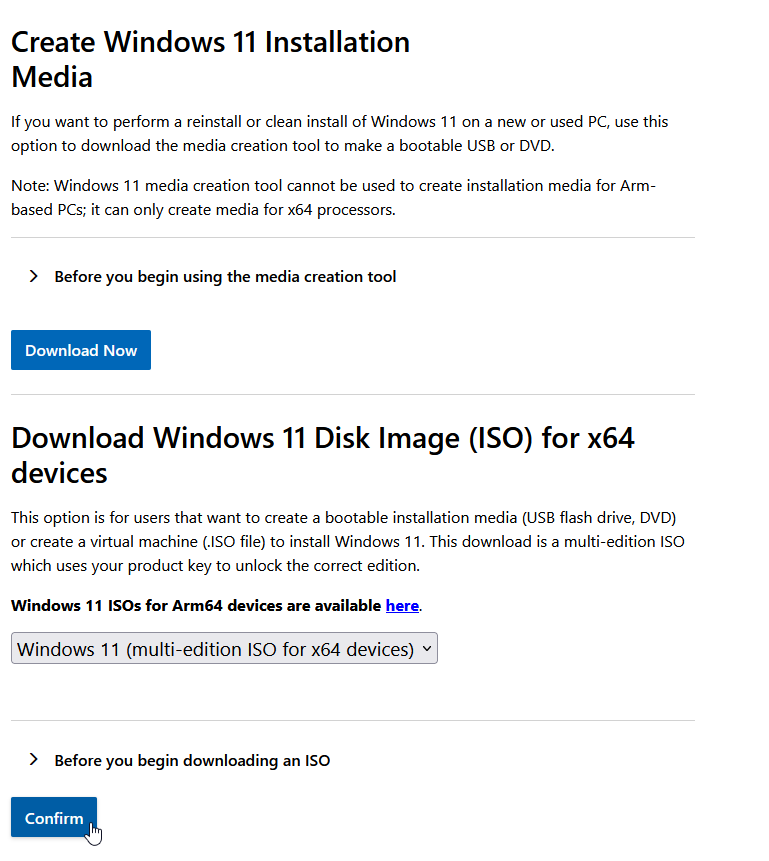
- Download (from Microsoft) the Windows 10 or 11 Media Creation Tool. Use this link to download the media creation tool directly from Microsoft. The media creation tool web page contains two options: ‘Update now’ and ‘Download tool now’. Do NOT click on ‘Update now’ because doing so would begin the update process on your computer. Since your goal is to deploy the upgrade to remote computers, instead please click on ‘Download tool now’ to save the tool to your computer. Important: When you run the media creation tool per the next step, you will not have a choice to select which Windows 11 version is used to create the media. This means that if Microsoft releases a new version of Windows 11 when you follow this tutorial, you’ll end up with that version as opposed to the specific version 23H2 that is available today at the time of this writing. If you have another channel for obtaining media for a particular Windows 11 version, such as with a Microsoft volume licensing agreement, you may use that instead of obtaining the media through the steps outlined in this tutorial.
- Open the Windows 10 or 11 Media Creation Tool that you saved to your computer a moment ago. IMPORTANT: It is NOT sufficient to run the tool as administrator (using right-click, run-as) from an account that is logged on without admin privileges. For reasons that aren’t fully clear, Microsoft requires that you *must* actually be logged on to the computer with an account that is a member of the local administrators group. Otherwise the tool will not allow you to run it to completion. We don’t know why Microsoft made the tool work this way, but it’s what they did, and presumably it’s for a good reason. So go ahead and log on to your computer as a local administrator, and then launch the tool and follow the rest of this tutorial.
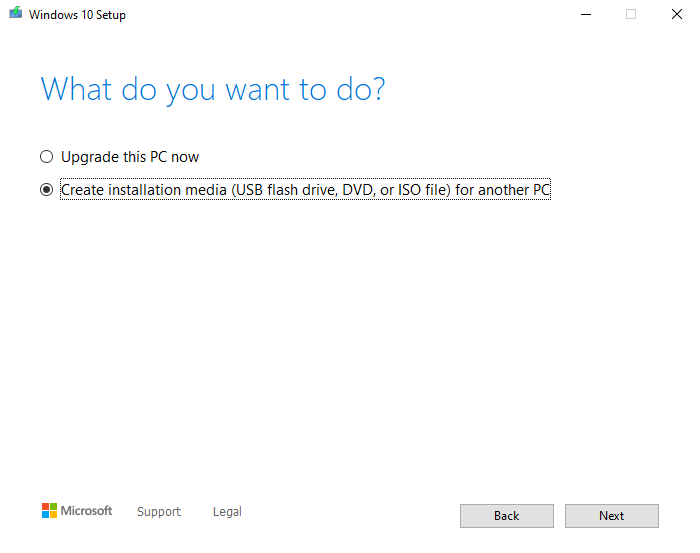
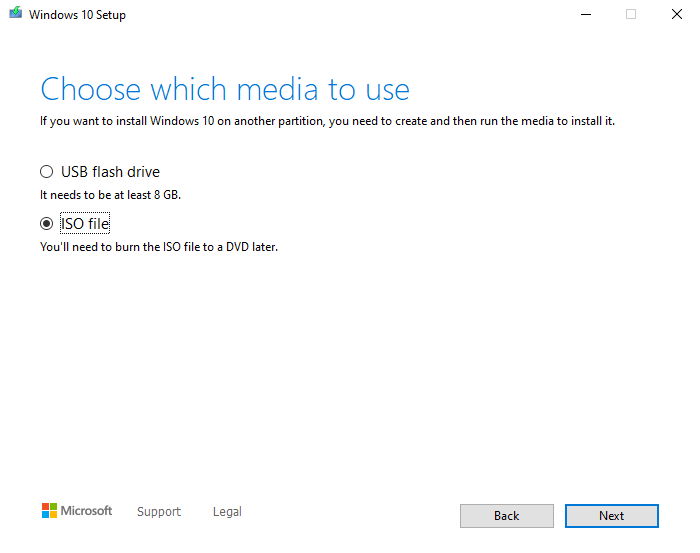
- Create installation media with the Windows 10 or 11 Media Creation tool. When the tool is running you’ll have to choose between two options to either ‘Upgrade this PC now’ or ‘Create installation media (USB flash drive, DVD, or ISO file) for another PC. Choose the option to ‘Create installation media…’ and then click ‘Next’.
- Choose your language / edition / architecture, and then click ‘Next’.

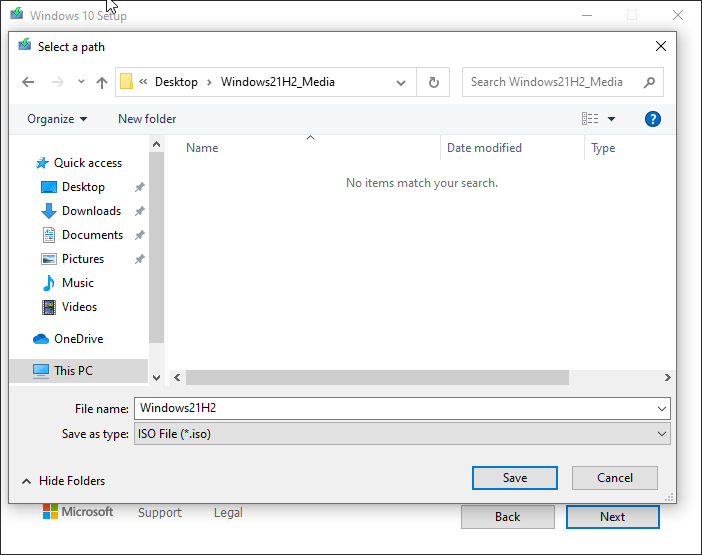
- Choose the media type. For the sake of this tutorial please select ISO as the type of media. After clicking the ‘Next’ button you will be prompted to choose a location on your computer to store the ISO file that will be downloaded/created. Select a directory/location to store the file, and then do something else until the download finishes. Depending on your connection speed it could take some time because it’s something like 4GB in size.
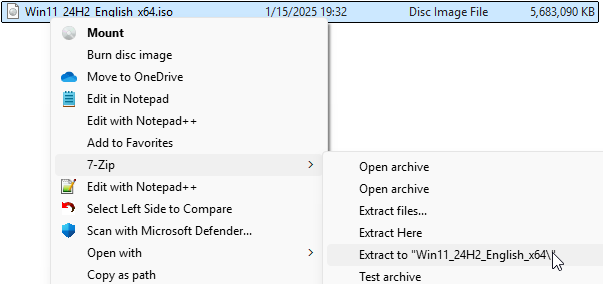
- Extract the ISO contents to a location on your local disk. After the download in the previous step is complete you’ll have to locate the file on disk and then extract the contents of the ISO to another folder. I like to use the free 7-zip for this process, but you may use whichever tool you prefer: 7-zip. After the ISO has been extracted you’ll have all of the installation files for the feature update in a single folder.
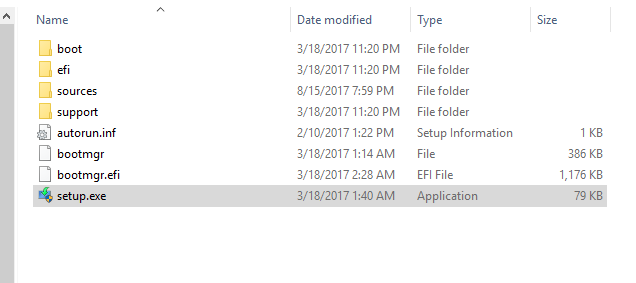
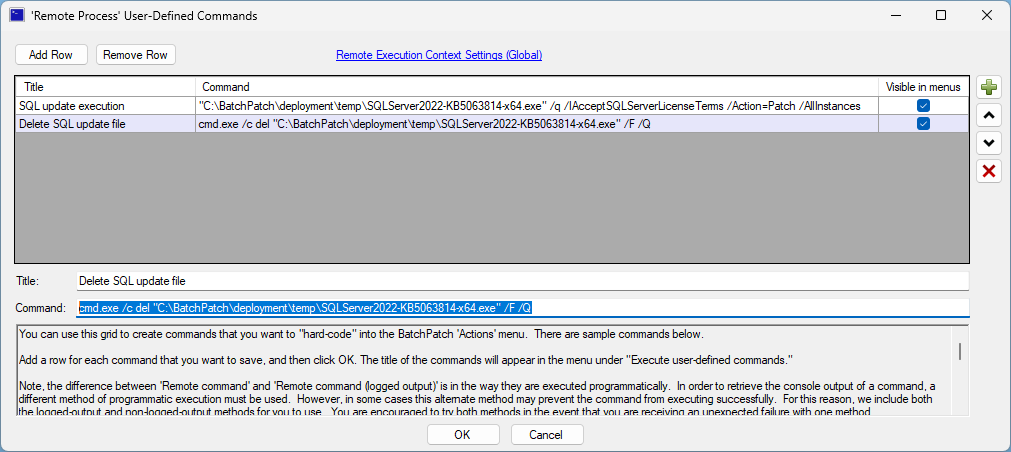
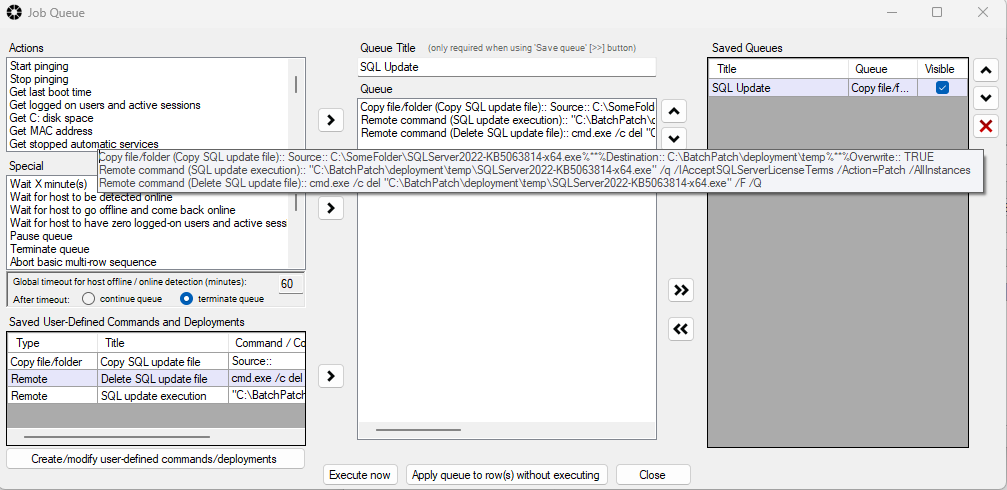
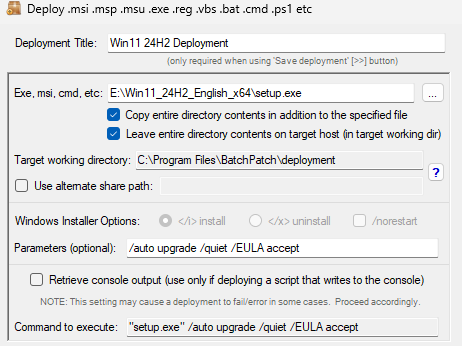
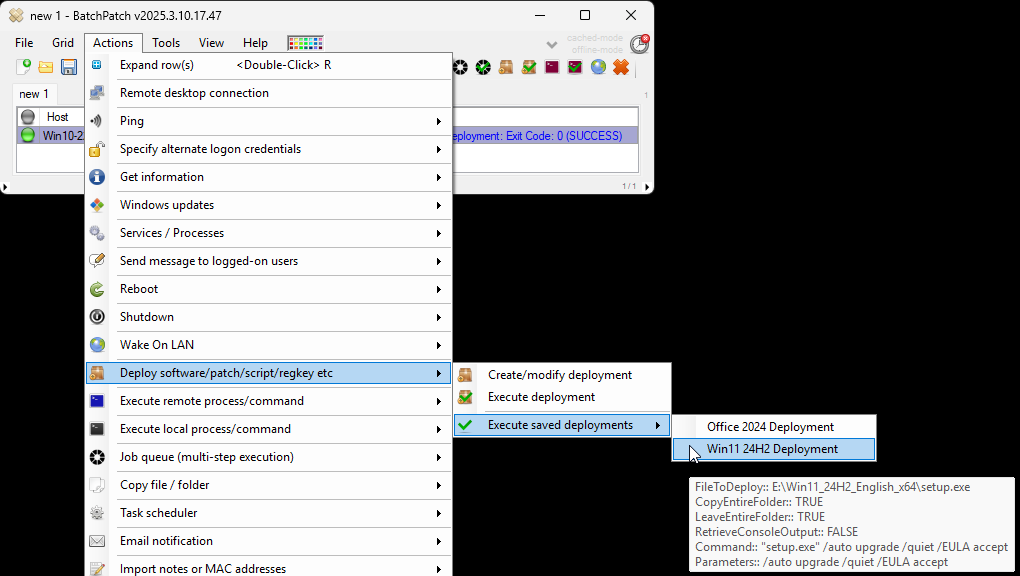
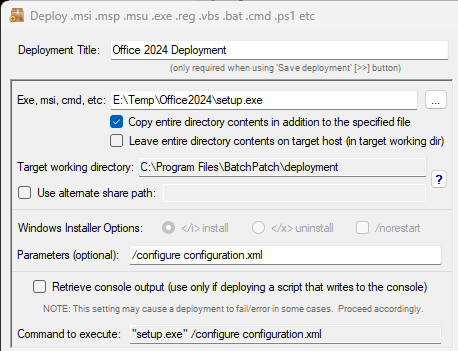
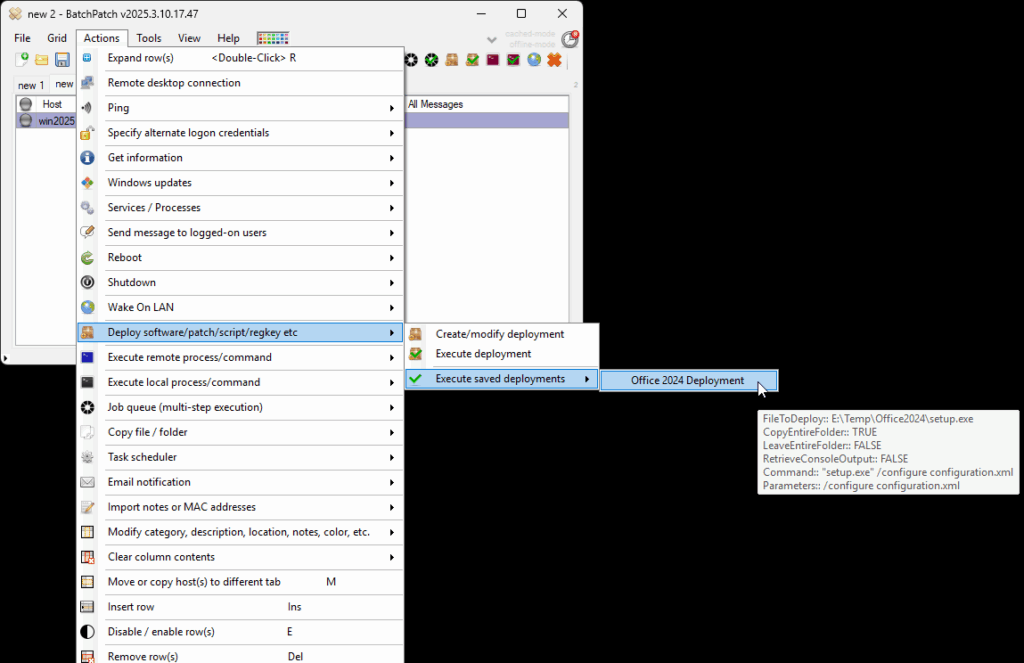
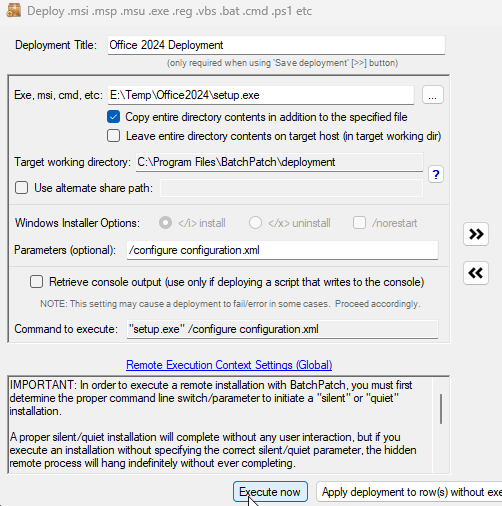
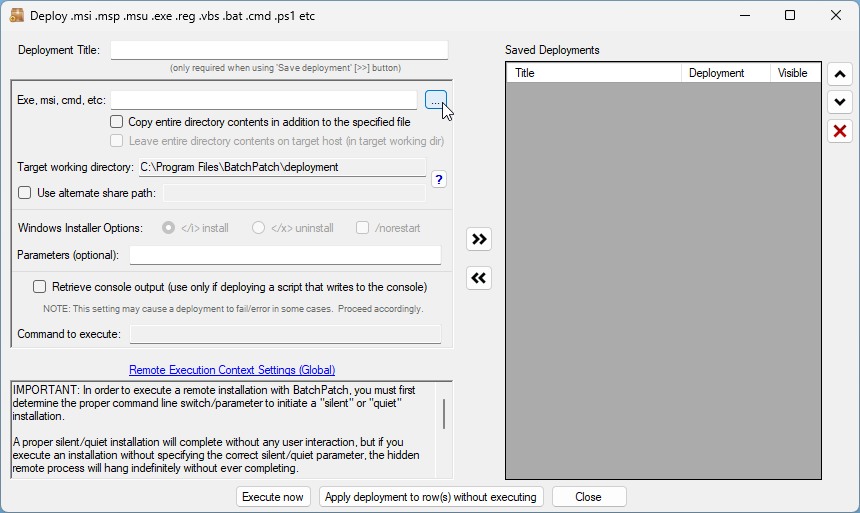
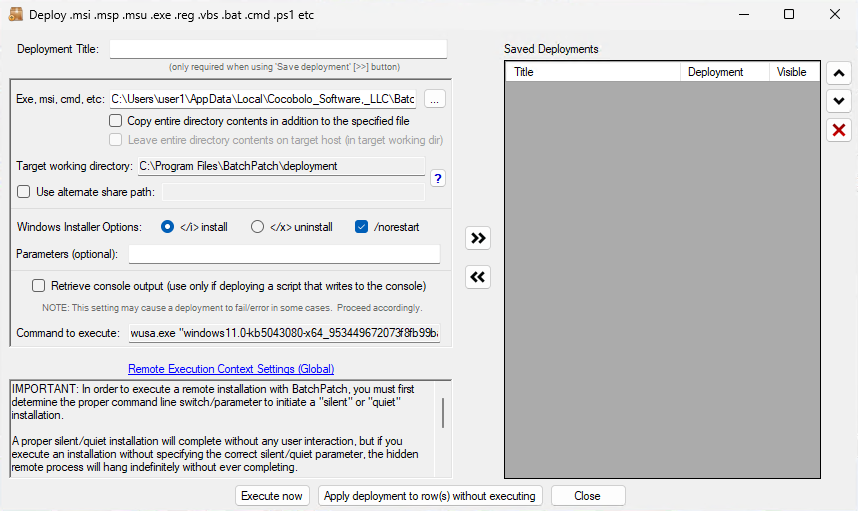
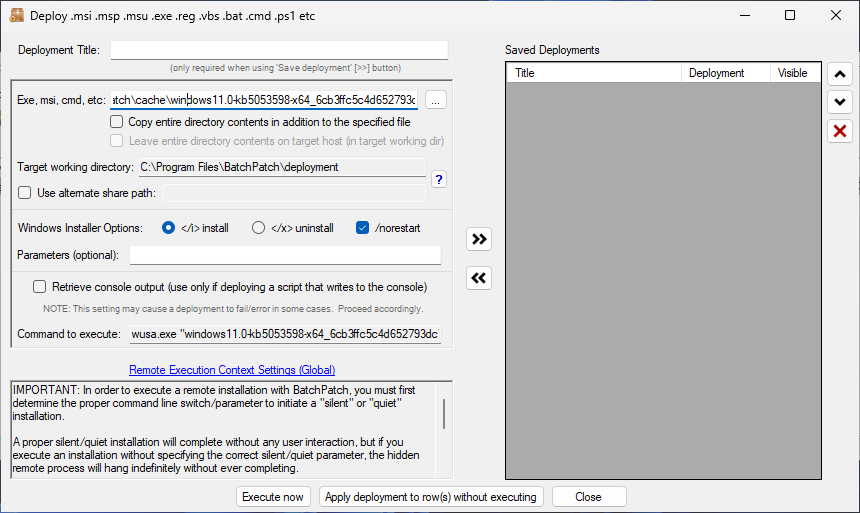
- Configure a deployment in BatchPatch. In BatchPatch click on Actions > Deploy > Create/modify. In the window that pops up for the Deployment configuration, click on the ‘…’ button to browse to the location where your ISO contents have been extracted to, and then choose the ‘setup.exe’ file as the file to deploy. Make sure to check the boxes for ‘Copy entire directory‘ and ‘Leave entire directory‘ . After the initial deployment phase is complete, the target Windows operating system will end up rebooting itself at least once but usually more than once while it completes the setup and installation for the feature update. As the process runs it needs to have access to all of the files that BatchPatch will deploy. Having both of the aforementioned boxes checked will ensure that when the upgrade process runs on the target computer that it has all of the files it needs for the installation. After the feature update has completed 100% you may delete the files from the target computer(s). However, please make absolutely sure that the upgrade process is 100% completed before you delete any files. In your BatchPatch deployment configuration screen you will also need to add the following parameters:
/auto upgrade /quiet
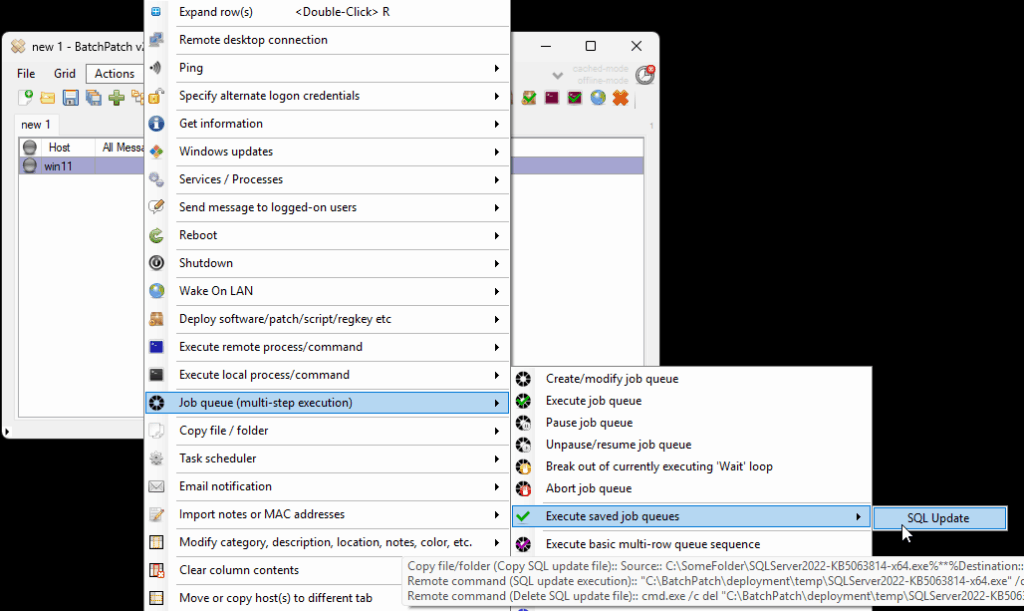
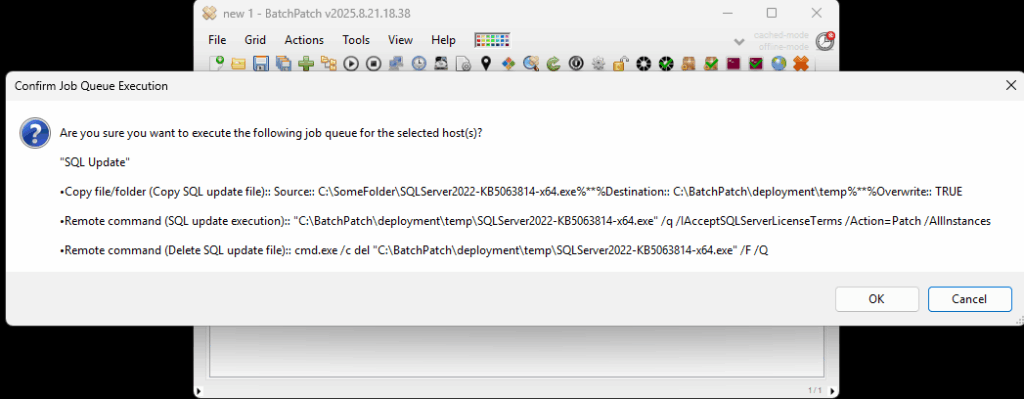
- Execute the feature upgrade deployment. In the deployment configuration that you created in the in the previous step you can execute the deployment immediately for the currently selected rows in the grid by just clicking on the ‘Execute now’ button. Alternatively you may save the deployment for future usage by clicking the double-right-arrow button ‘>>’. If you choose to save the deployment instead of executing it immediately, then when you are ready to deploy the feature update to your remote computers, you can begin the process by selecting those computers in the BatchPatch grid and then clicking on Actions > Deploy > Execute deployment, and then choose the deployment that you just created/saved.
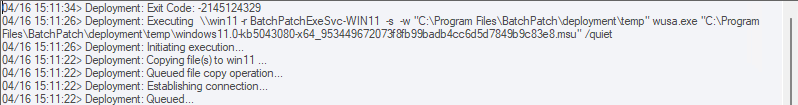
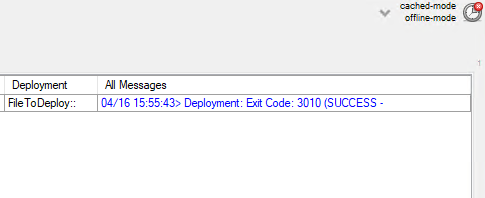
You should expect that the entire process will take a bit of time to complete. BatchPatch has to copy the whole installation directory to the target computer(s), which contains several gigabytes, before it can execute the upgrade process on the target(s). IMPORTANT: After the BatchPatch deployment completes for a given target computer BatchPatch will show Exit Code: 0 (SUCCESS). However, this just means that the BatchPatch deployment component is finished. The Windows feature update/upgrade process will take additional time. Please be patient and let the target computer continue upgrading and rebooting as many times as is needed. It might take a little while with multiple automatic reboots before everything is 100% finished.
NOTE: We have had a couple of reports from users who received the following error:
Deployment: Error: Access to the path '\\TargetComputer\C$\Program Files\BatchPatch\deployment\autorun.inf' is denied.
We don’t know the exact cause of this issue, but it seems likely to somehow be related to the way that permissions were applied or inherited during the ISO extraction process. If you encounter this error it can be resolved quickly and easily by just deleting the autorun.inf file from the source directory after extracting the ISO contents but before executing the actual deployment for any target computers. This will prevent the problematic file from ever being copied to target computers. As such, the error will not occur.