In the July 2022 version of BatchPatch we added integration for Microsoft’s Local Administrator Password Solution (LAPS), so now you can easily highlight a group of target computers in your BatchPatch grid and then retrieve the LAPS password stored in Active Directory for each of the selected hosts/rows. The rows will then be automatically populated with the corresponding LAPS username/password for each selected host.
If you’re reading this tutorial then you probably already know what LAPS is, but in case you don’t… Microsoft describes that the “Local Administrator Password Solution” (LAPS) provides management of local account passwords of domain joined computers. Passwords are stored in Active Directory (AD) and protected by ACL, so only eligible users can read it or request its reset. You can download LAPS here. Microsoft provides a complete configuration tutorial for LAPS here.
The installation and configuration process for LAPS is actually pretty quick and painless. Follow Microsoft’s instructions or pick another tutorial on the web (there are many). Once you have it working, it’s very easy to import logon account information from LAPS into BatchPatch.
- Highlight the rows in the BatchPatch grid for which you want to retrieve the LAPS password from Active Directory
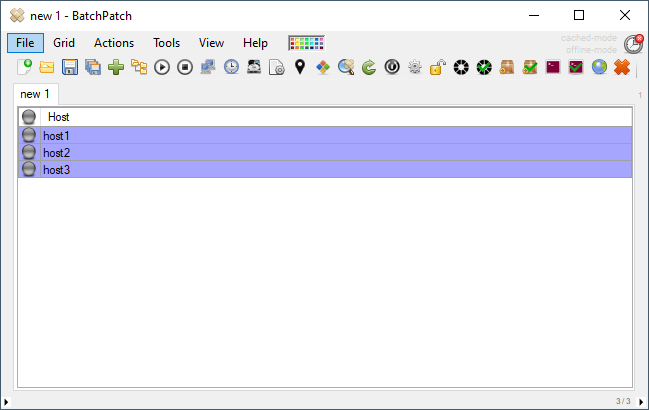
- Select Actions > Specify alternate logon credentials > Get LAPS password from Active Directory…
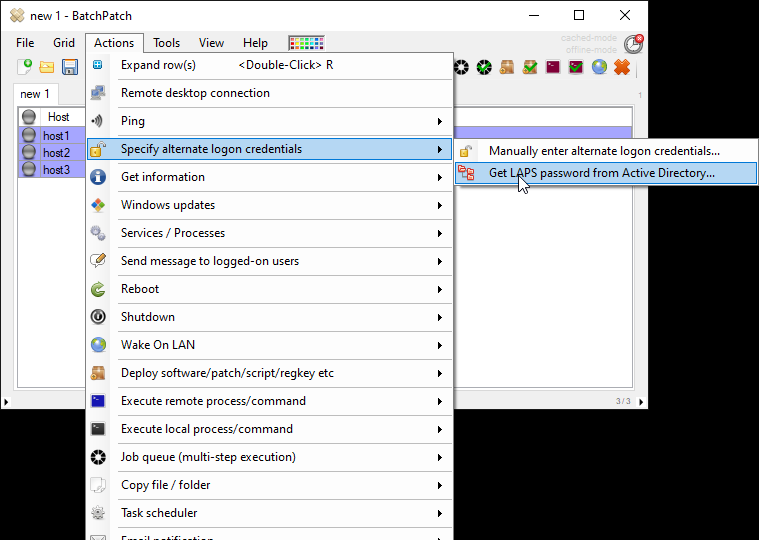
- In the Get LAPS Password form you have to first enter the LAPS username. This is the name of the local administrator account being managed by LAPS for a given computer. When LAPS is configured for an organization, there is a Group Policy, Computer Configuration\Administrative Templates\LAPS\Name of administrator account to manage, that tells LAPS which local administrator account it should manage. Since LAPS only stores the actual password value in Active Directory, you need to tell BatchPatch the username so that when BatchPatch retrieves the password from Active Directory, it can then be inserted with the username into the Alternate Credentials field for a given row. It’s probably the case that in most environments the LAPS username will just be administrator, but of course it really all depends on your particular environment and how LAPS has been configured.
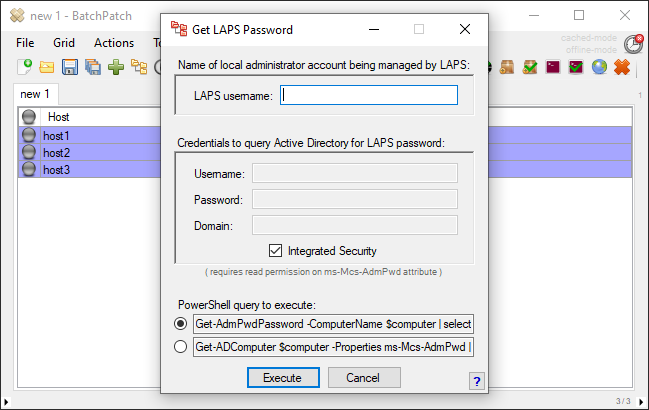
- You’ll also have to specify the credentials that BatchPatch should use to query Active Directory for the LAPS password values. When BatchPatch runs the PowerShell query to retrieve the LAPS password for a given computer, it needs to run under an account that has read/view permission on the ms-Mcs-AdmPwd attribute for that computer in Active Directory. If you choose Integrated Security instead of supplying credentials, BatchPatch will execute the query as the account being used to run BatchPatch. If you instead specify credentials here, note that these credentials are *not* saved to disk, but they will be remembered for the life of this BatchPatch.exe instance. When you close and re-open BatchPatch you will be required to re-enter the credentials.
- Finally, you’ll need to select the PowerShell query to execute.
Get-AdmPwdPassword requires the Local Administrator Password Solution (LAPS) PowerShell module, AdmPwd.PS, to be installed on the BatchPatch computer.
Get-ADComputer requires the Remote Server Administration Tools (RSAT) Active Directory module to be installed on the BatchPatch computer.Both of the above queries accomplish the same task, so you can simply pick the one for which you already have the required toolset installed.
That’s pretty much all there is to it. When you click Execute BatchPatch will connect to Active Directory and retrieve the LAPS password for each of the selected rows in the grid, and then BatchPatch will insert the corresponding password along with the LAPS username into the Alternate Credentials field for each selected row in the grid.

