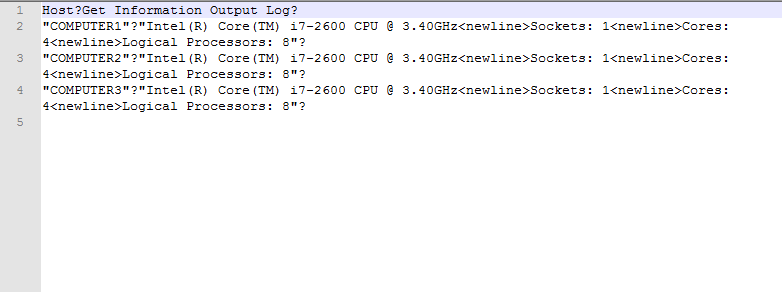
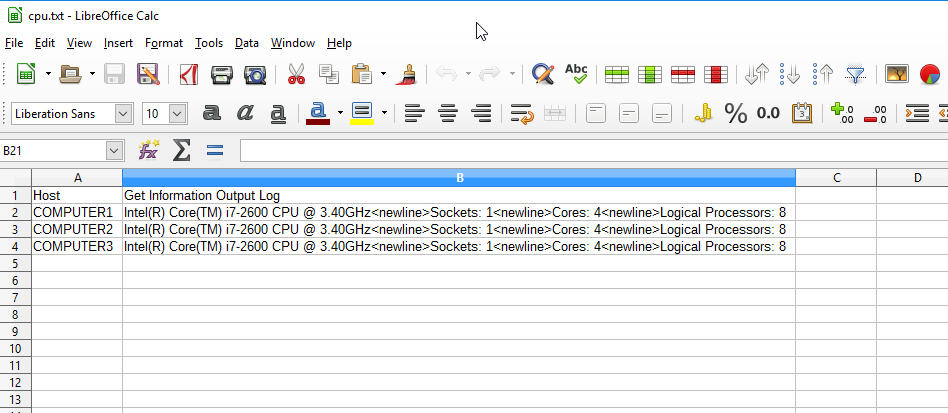
In order for a custom deployment to be successful, you might not be able to use absolute paths inside of a script where those paths point to a location on a remote server. This is dependent upon the particular situation, but if you’re having problems successfully deploying a script that makes calls to other scripts or executables stored on a remote server, below I will show you how to ensure success.
Example:
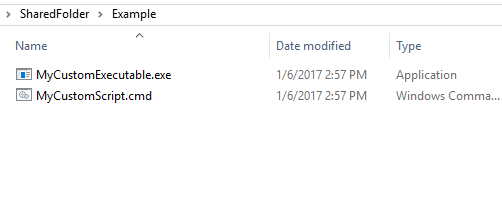
Imagine you have a remote server folder:
\\RemoteServer\SharedFolder\Example |
The folder contains two files – MyCustomExecutable.exe and MyCustomScript.cmd:
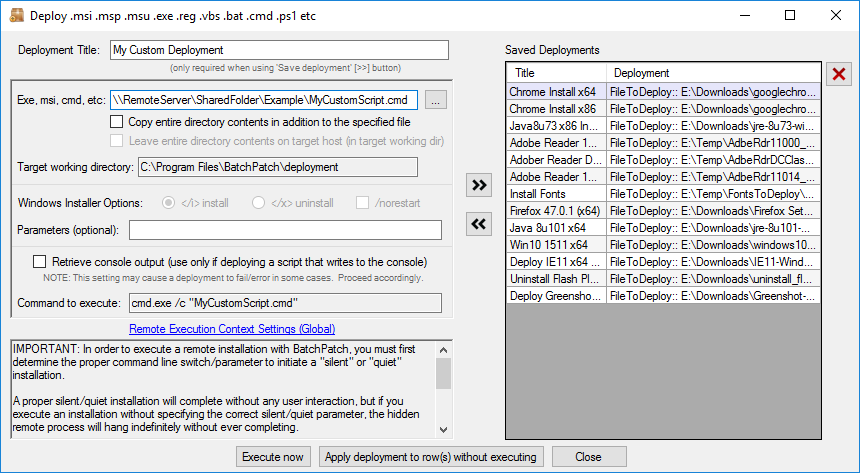
The contents of the script are as follows. Note, the script makes a call to execute the MyCustomExecutable.exe using an absolute path to the server location where the exe file currently resides:
@ECHO OFF ECHO *** Executing My Custom Script With Remote Server Absolute Paths *** "\\RemoteServer\SharedFolder\Example\MyCustomExecutable.exe" |
You are attempting to deploy the script using the configuration in the screenshot below, but you are not having success:
If you are having problems getting the deployment to run successfully, you have a couple of options to try:
- You might be able to get the deployment to execute successfully simply by modifying the ‘Remote Execution Context’ settings. In the screenshot below you can see that I have launched the ‘Remote Execution Context’ settings window directly from the deployment configuration screen. However, you can also get to the ‘Remote Execution Context’ settings by clicking ‘Tools > Settings > Remote Execution.’
The default configuration is set to use the SYSTEM account for remote execution. This is usually the best for most situations, but one drawback to this setup is that the SYSTEM account does not have access to network resources. Since the script that gets executed on the target system is currently set to make a call to a remote server location (“\\RemoteServer\SharedFolder\Example\MyCustomExecutable.exe”), the deployment will fail because the SYSTEM account on the target computer will not be able to reach that network resource. Try running your deployment with ‘Elevated token’ or ‘Normal’ and see if you have success. If not, set the Remote Execution Context setting back to ‘SYSTEM’ and go to the next step.

- With a simple adjustment to your script and your BP deployment configuration you can remove any network calls so that the entire deployment executes locally on the target system.
A. Modify your script to remove the absolute path. See below for example:@ECHO OFF ECHO *** Executing My Custom Script WITHOUT Remote Server Absolute Paths *** "MyCustomExecutable.exe"
B. Modify your deployment configuration by ticking the box that says “Copy entire directory contents in addition to the specified file”
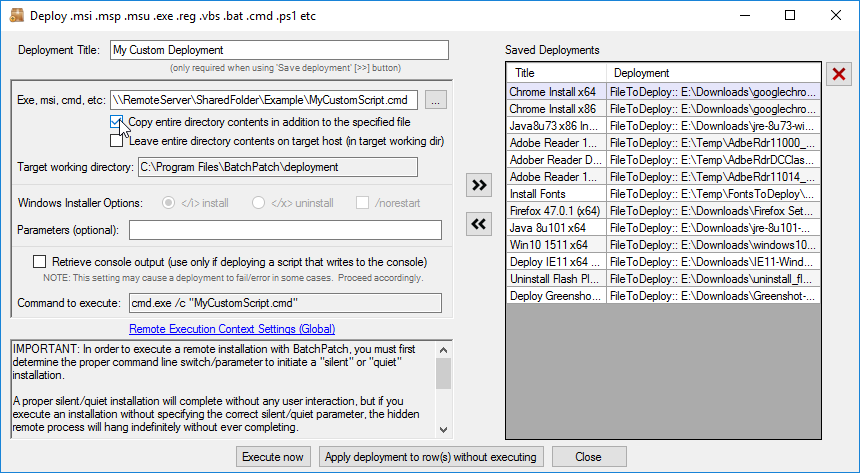
C. Now when you execute the deployment, the entire folder contents of (\\RemoteServer\SharedFolder\Example) will be copied to the target systems. Then when the script is executed, since it now contains a relative path to the MyCustomExecutable.exe, it will find that file in the same temp deployment directory as the script is being executed from. The deployment will complete successfully (unless, of course, the reason for it failing in the first place was due to some other unrelated issue).