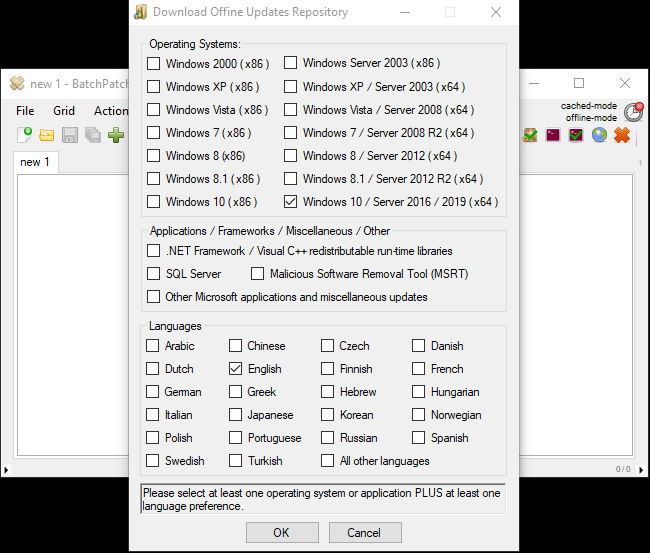
The Ultimate Windows Update Tool
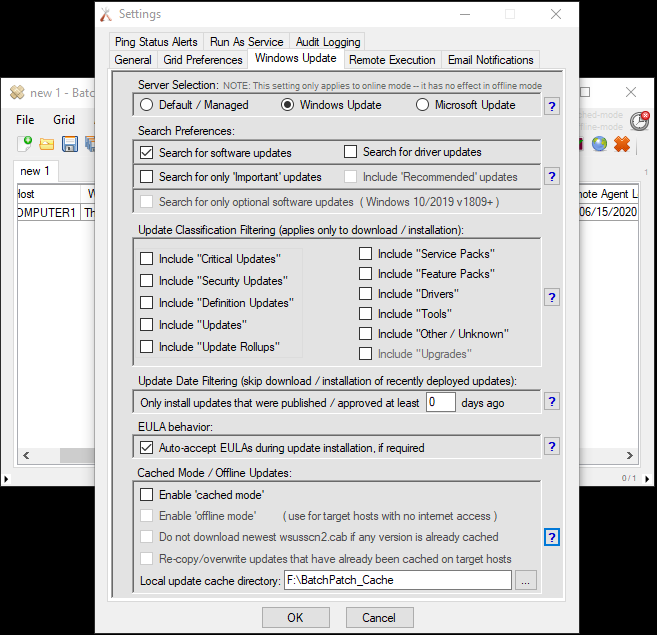
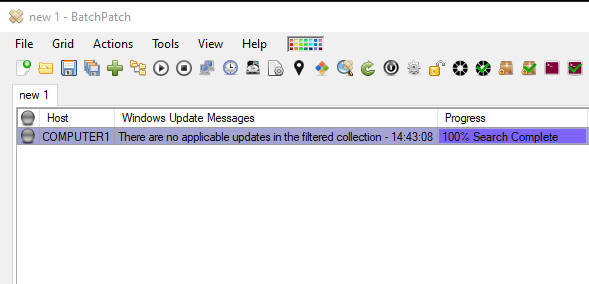
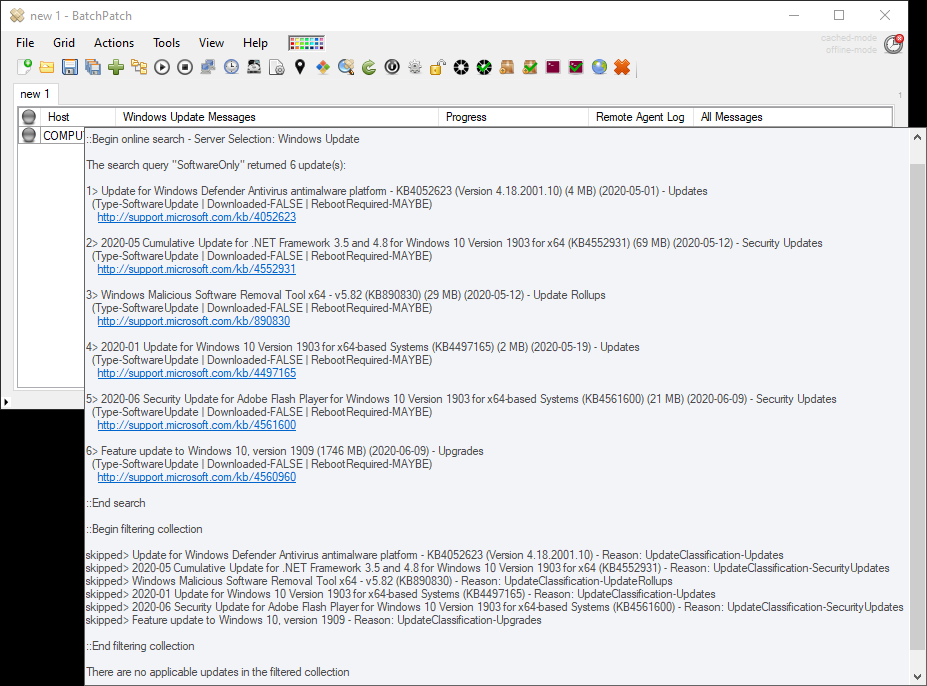
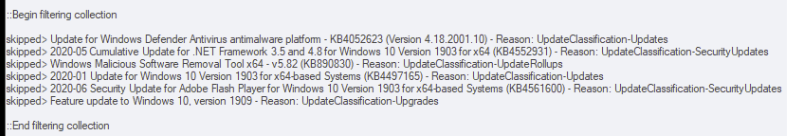
BatchPatch is the “Ultimate Windows Update Tool” for a reason. It’s inexpensive, it’s very easy and intuitive to use, and it “just works” when it comes to updating Windows. It can be used to apply standard Windows Updates in addition to managing patch deployments and software updates for third-party applications.
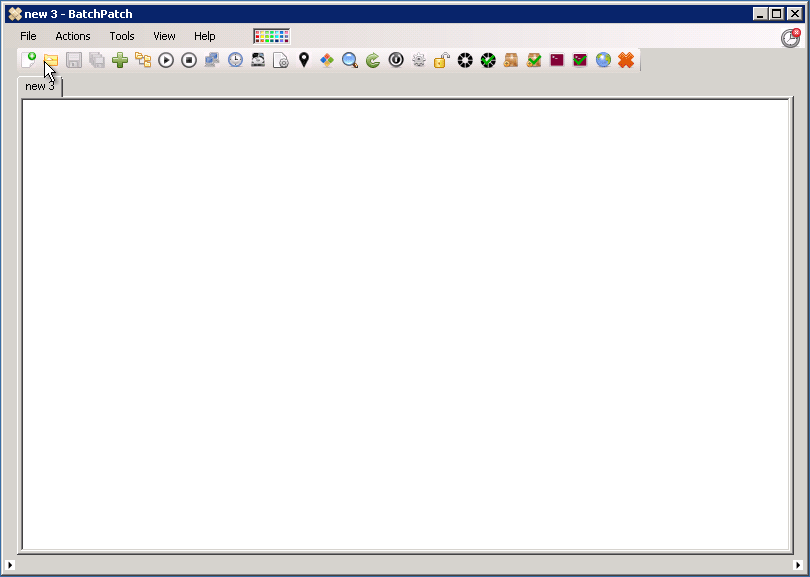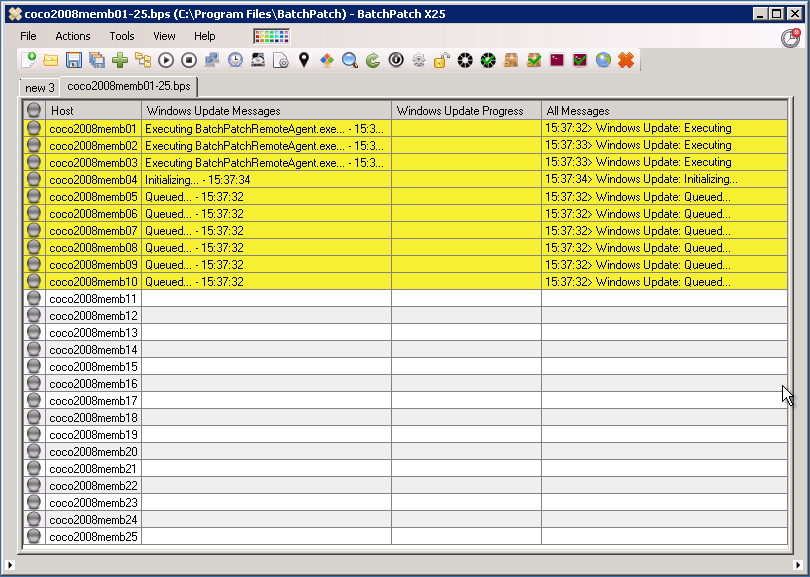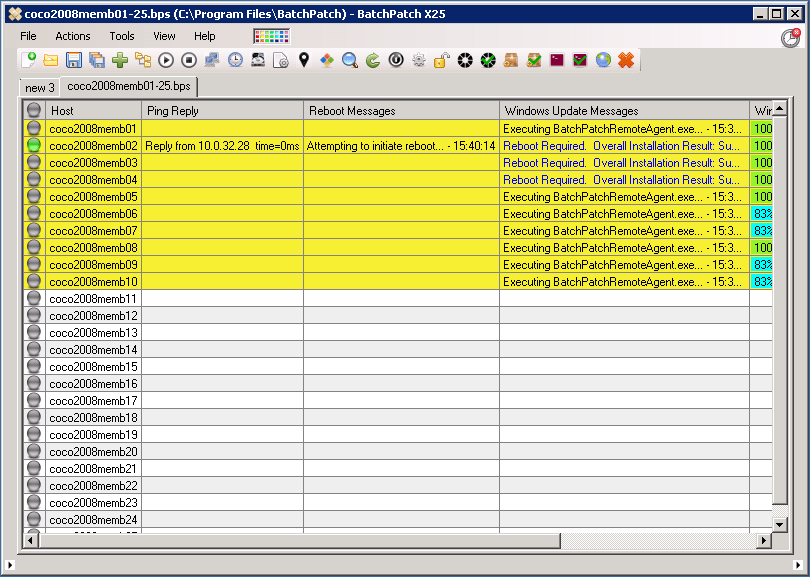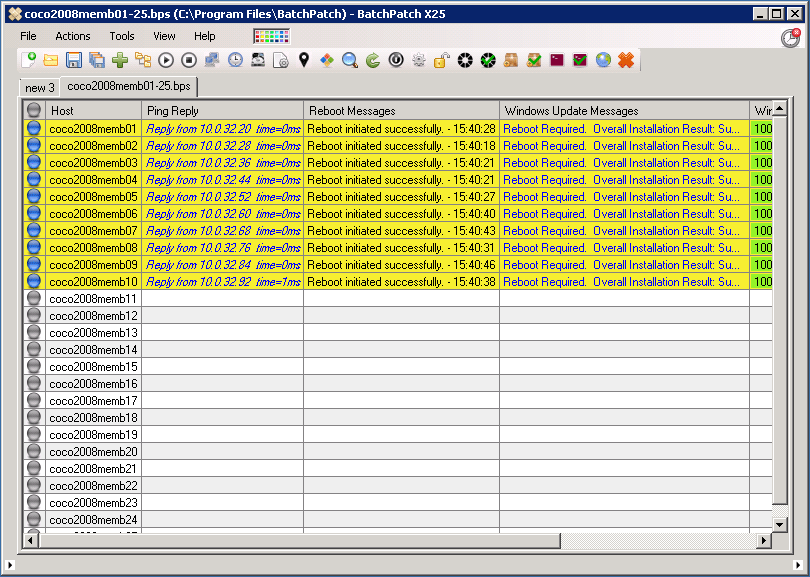
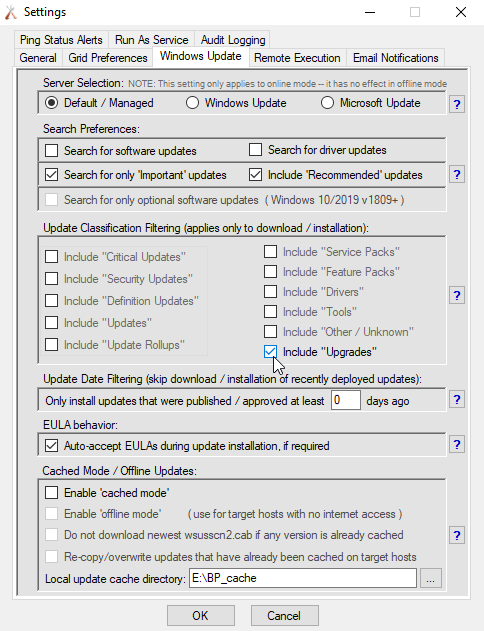
A Tool Designed for Systems Administrators
Systems administrators love BatchPatch because it was designed specifically for them, with a simple, straightforward interface that works in a way that “just makes sense” to people who work with computers for a living. A wise sysadmin once compared BatchPatch to a fighter jet, whereas some other Windows patch management applications can seem more like an aircraft carrier. We think the analogy is a pretty fair assessment. Some patch management software products can be extremely complicated and expensive to operate. They are slow moving and hard to steer. Their setup typically involves numerous servers with lots of moving parts, which can not only cost a lot of money but can also be a massive time sink for the administrators. They’re bloated, difficult to operate, and frustrating to troubleshoot. While it’s true that they will often offer a ton of different features, in many environments they are just way too much to deal with, especially when only a small subset of the features are typically even utilized. BatchPatch, on the other hand, is able to just swoop in rapidly with high maneuverability to hit the needed targets, and then get out quickly. The patching is completely done practically before it even started. We have many customers who have either completely switched to BatchPatch from these behemoth applications, or who have added BatchPatch as a supplementary tool for those times when they simply need to “get it done” without wasting hours struggling with their standard patch management tool.
Free Evaluation
If you’re new to BatchPatch, please download the free evaluation version so that you can test the software for yourself. In many environments it will “just work” right out of the box with zero configuration required. In those cases you can literally download the app, launch it, and start patching within seconds. In some environments BatchPatch will require a minimal amount of configuration to setup the proper permissions and firewall rules to get going. Have a look at the ‘Getting Started‘ page for details on how to setup your environment to work with BatchPatch.
Instructional Materials and Tutorials
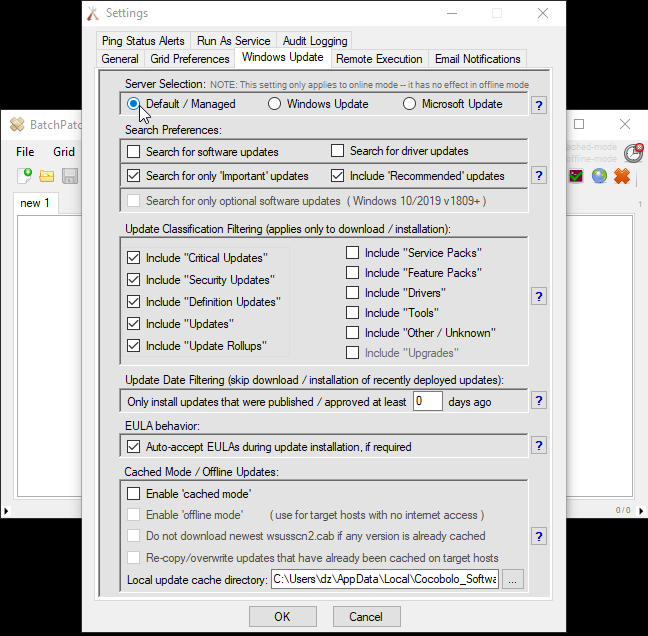
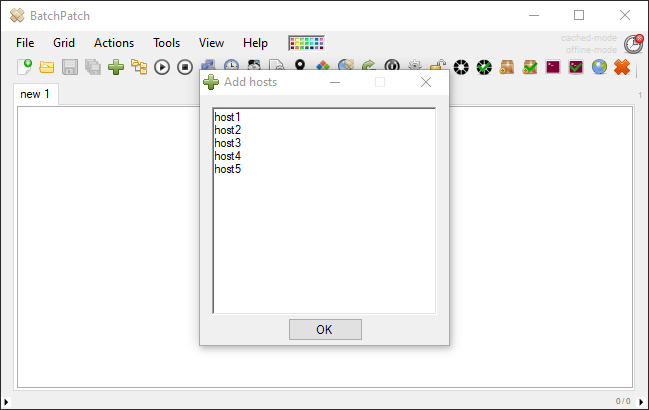
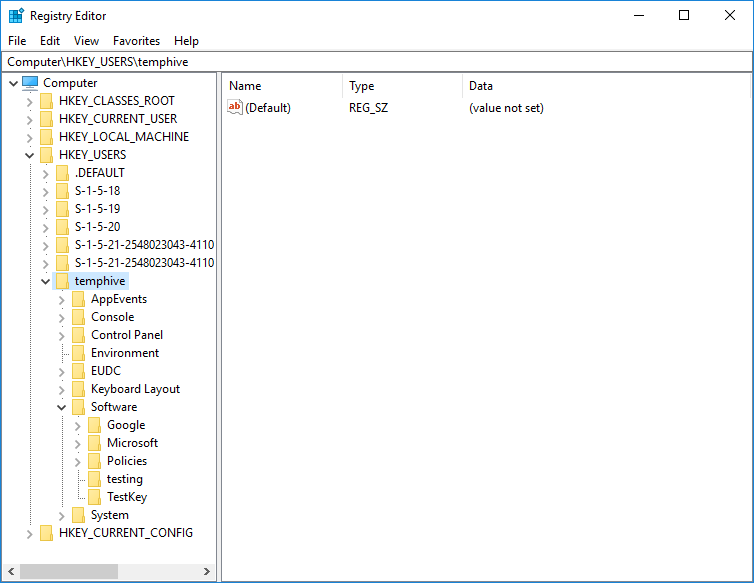
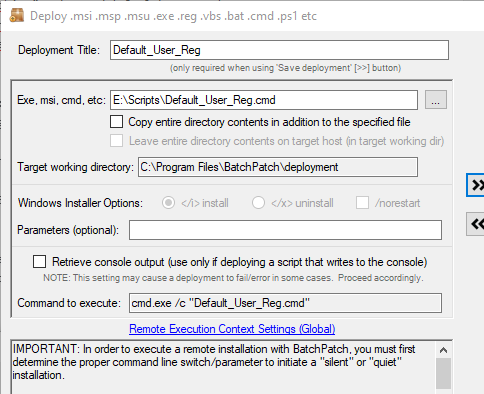
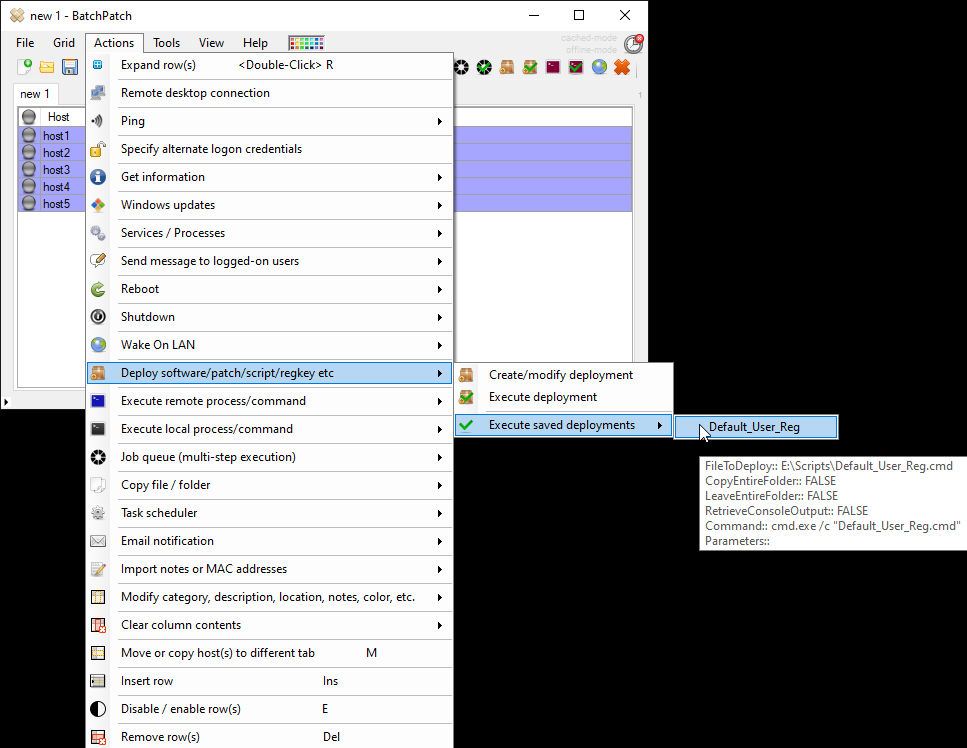
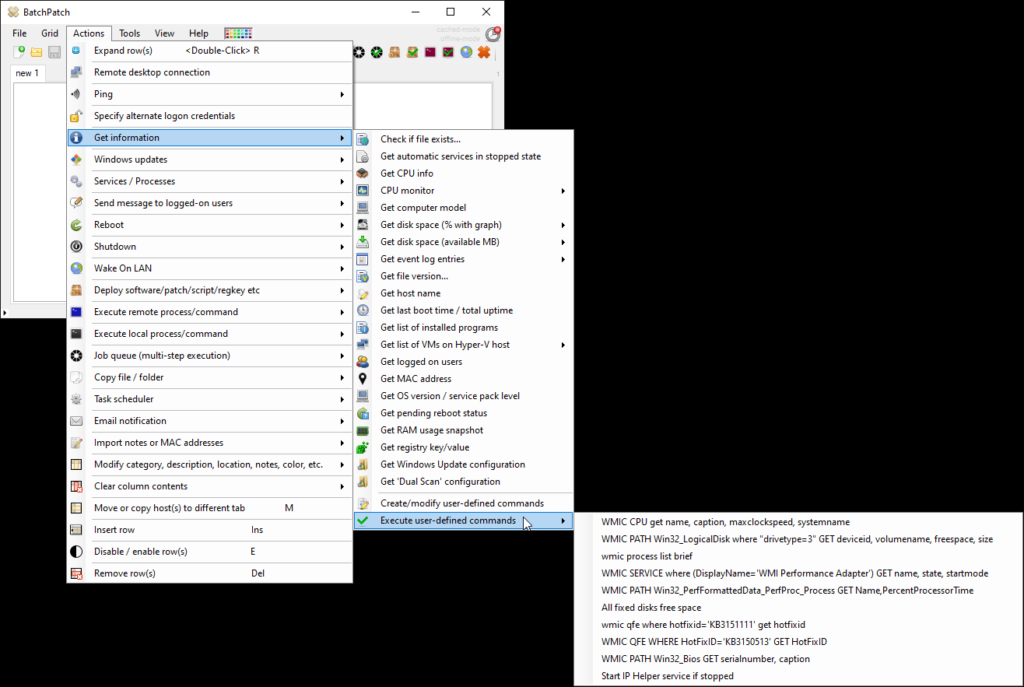
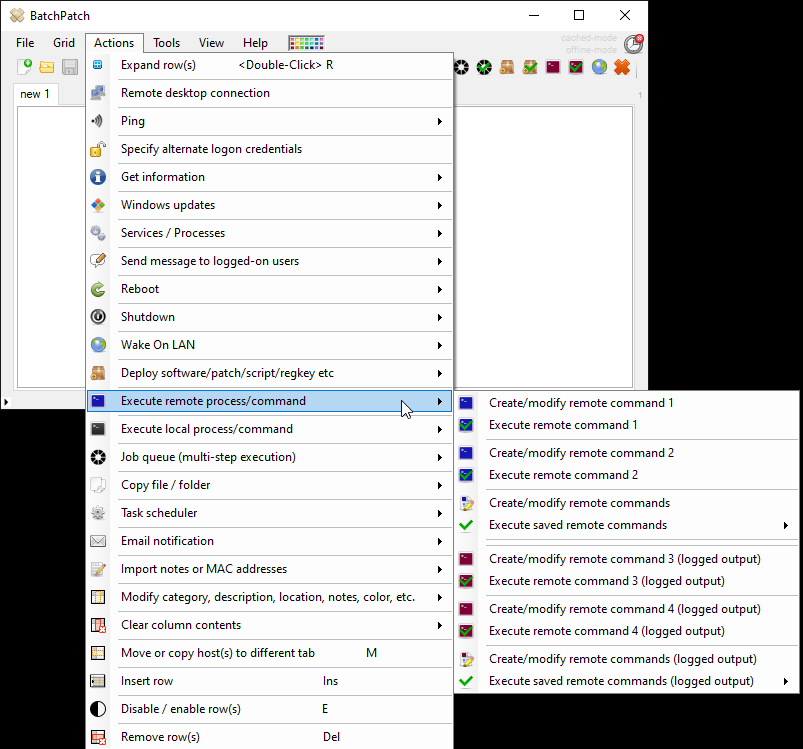
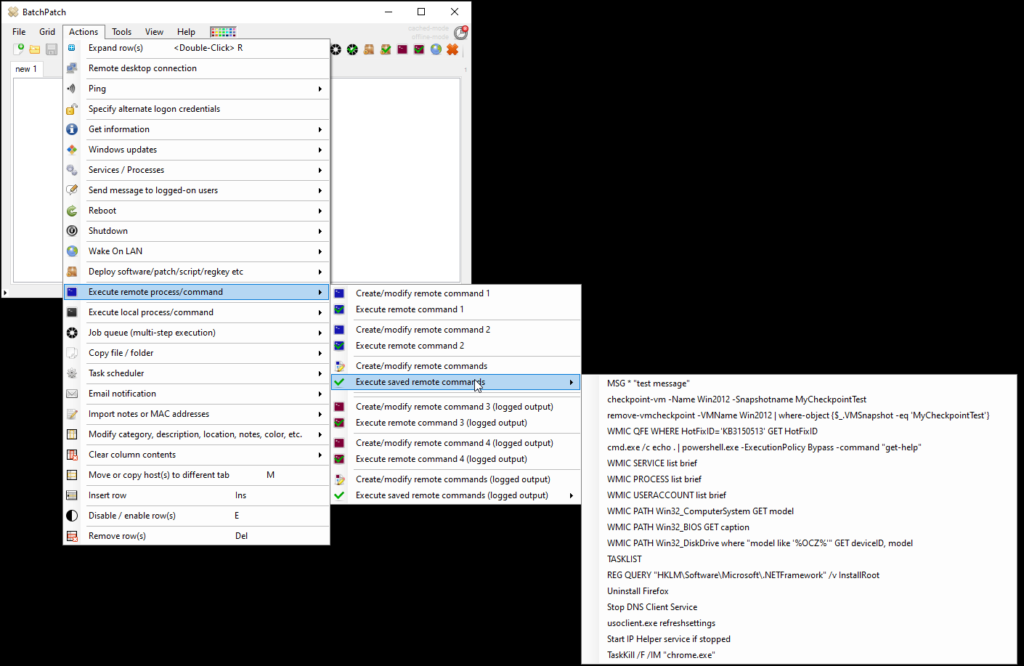
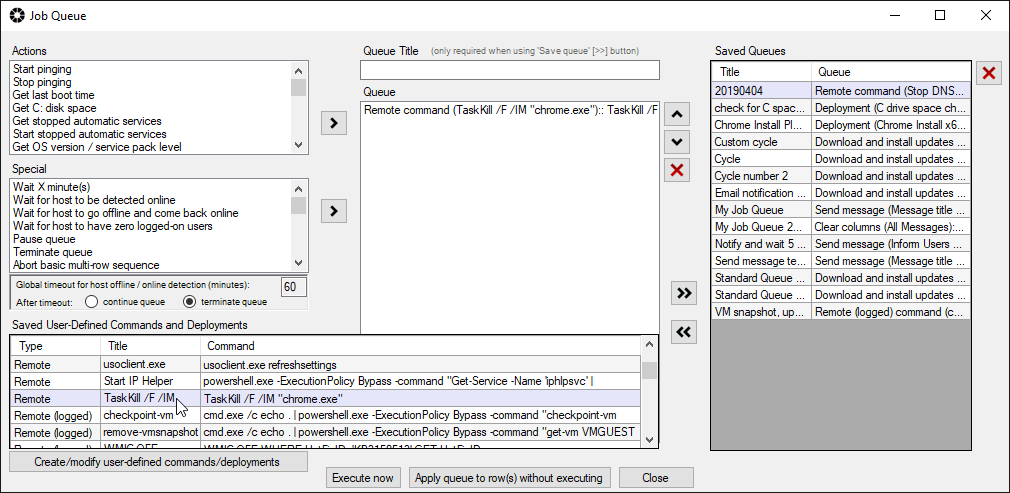
We have numerous tutorials and instructional materials posted here, that will help you get the most out of BatchPatch, whether you just want to apply Windows Update to numerous computers, or if you need to deploy 3rd-party software to your entire network, or even if you need to orchestrate a complex sequence where target servers are patched and rebooted in a specific order, with scripts executed before and after patching, and with detailed requirements for which machines are offline at any given time.
Help and Troubleshooting
If you encounter any problems, have a look at these troubleshooting pages:
Troubleshooting Common Errors in BatchPatch
BatchPatch Troubleshooting Guide
Forums
You may also search the forums for help, or post a question there if you can’t find the answer you’re looking for.
Contact us
And of course you may also reach out to us directly with any questions or concerns.