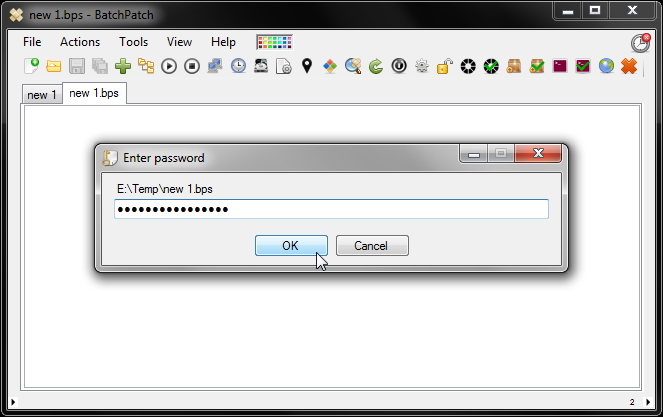
In the November 2015 release of BatchPatch one of the cool new features is password protection with 256-bit AES encryption for your saved .bps / .bpt files. What does this mean? The contents of a .bps / .bpt file can be password encrypted such that after you have applied a password to a particular grid, when you save that grid, the contents will be encrypted on disk. Then later when you load the saved grid file into an instance of BatchPatch you will be prompted to enter the password to unlock/decrypt the file contents to be displayed in the grid.
Why might an administrator want to use this feature? In particular, if you are storing sensitive passwords in any of your .bps / .bpt grid files, this feature might be important to you. In BatchPatch if you’re using ‘Integrated Security,’ which means that you are launching the BatchPatch.exe in the context of a user that has been granted local administrator privileges on target computers, then you probably do not have any passwords stored in a grid or a saved .bps / .bpt file. However, for those of you who are using ‘Alternate Credentials’ in BatchPatch, which means that you have specified particular logon credentials for a given row/host or set of row(s)/host(s), this new feature might be just what you were looking for to increase overall security.
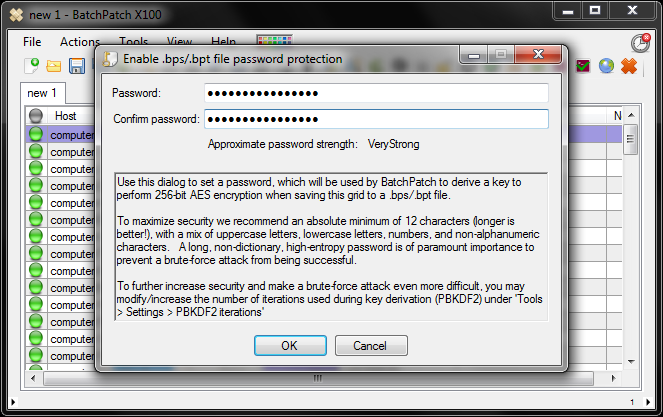
To add password protection to a grid simply click on ‘File > Password protect .bps/.bpt file contents…’ You will be presented with a dialog that enables you to apply a password to that grid, and then you’ll be prompted to save the grid.
To maximize security we recommend an absolute minimum of 12 characters for your password, though even longer is better! A good password should also contain a mix of uppercase letters, lowercase letters, numbers, and non-alphanumeric characters. A long, non-dictionary, high-entropy password is of paramount importance to prevent a brute-force (password-guessing) attack from being successful. Even though the encryption itself can’t be “cracked” per se, your password *can* be guessed, especially when it’s short and low-entropy. And when you’re using one password to protect a file that contains many other passwords, we strongly recommend using a very long, unpredictable password.
To further increase security and make a brute-force (password-guessing) attack even more difficult and time consuming, you may modify/increase the number of iterations used during key derivation (PBKDF2) under ‘Tools > Settings > PBKDF2 iterations.’