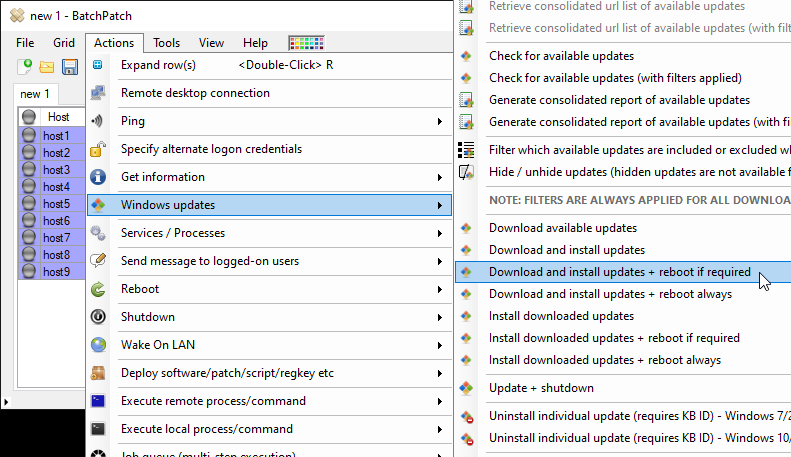
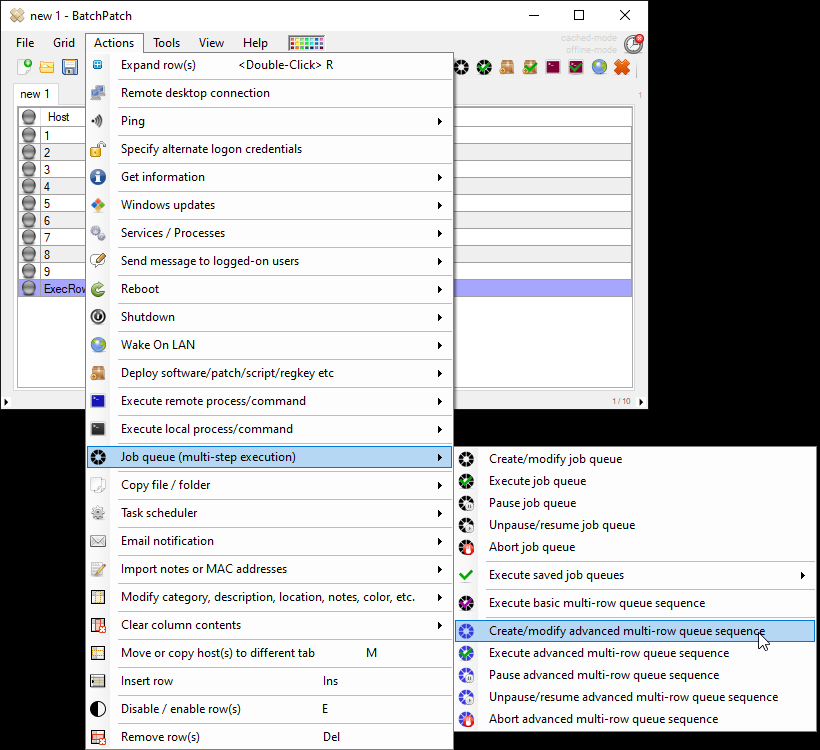
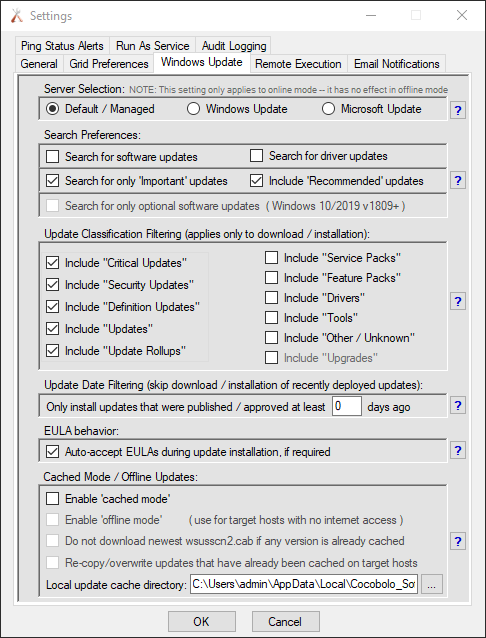
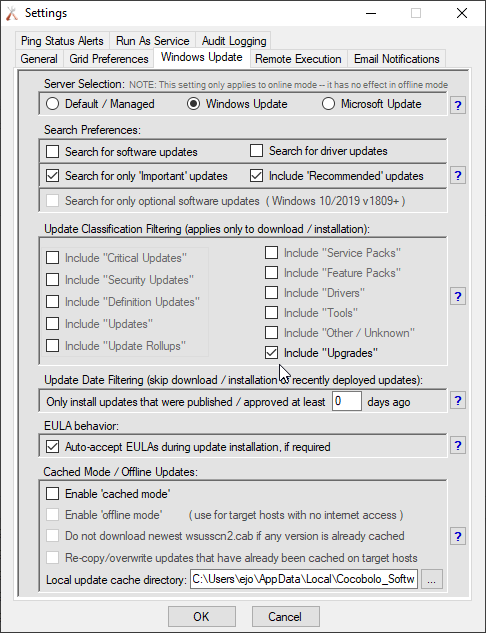
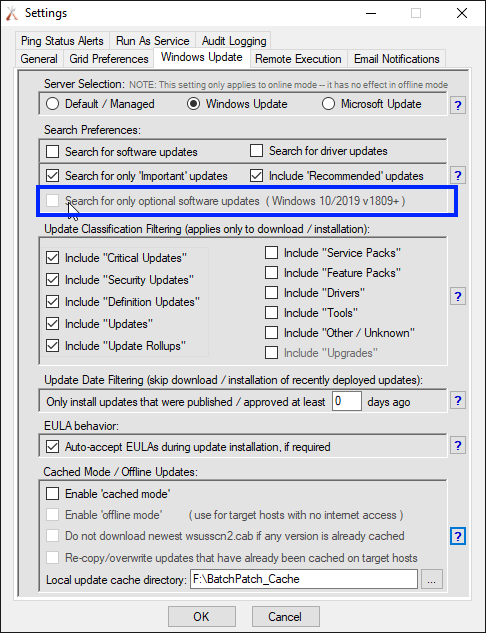
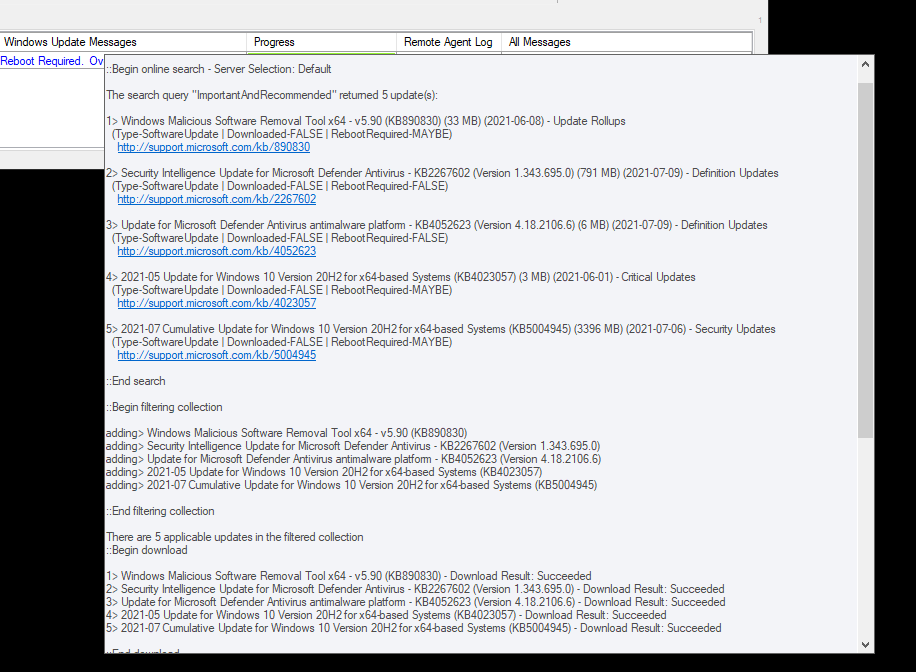
In BatchPatch you can trigger the Windows Update and reboot process on numerous computers all at the same time. Select the desired target computers in the grid, and then click on ‘Actions > Windows updates > Download and install updates + reboot if required‘
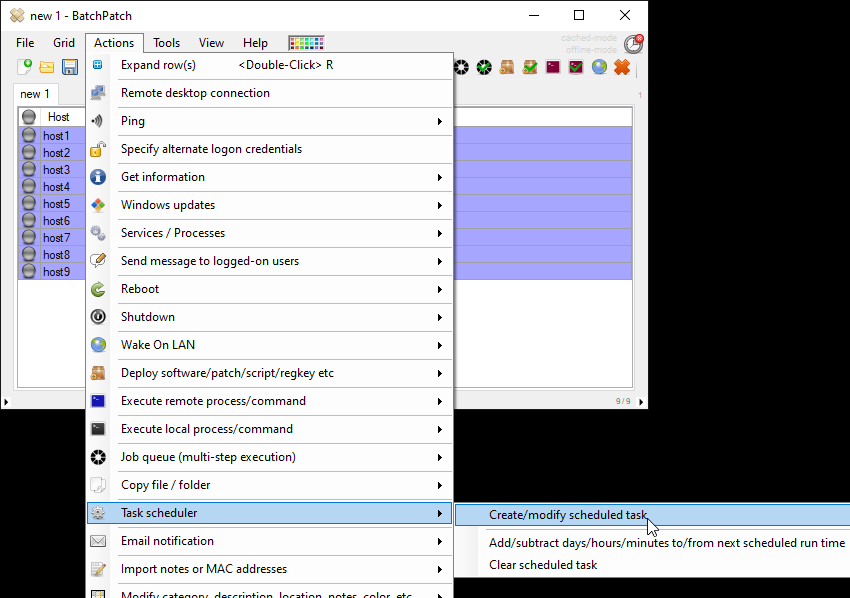
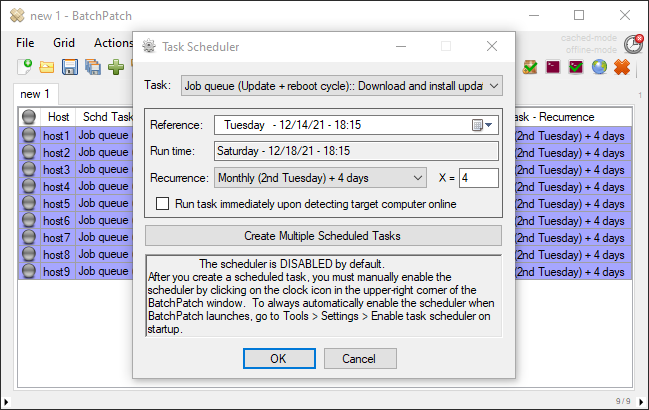
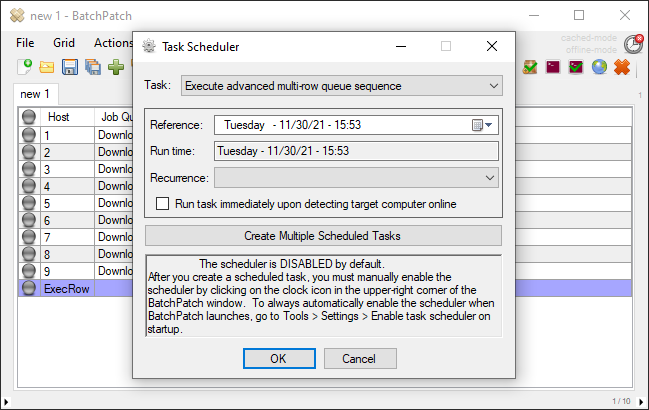
If you want this to occur automatically every month at a scheduled time, you can instead create a scheduled task to do the same thing. Select Actions > Task scheduler > Create/modify scheduled task
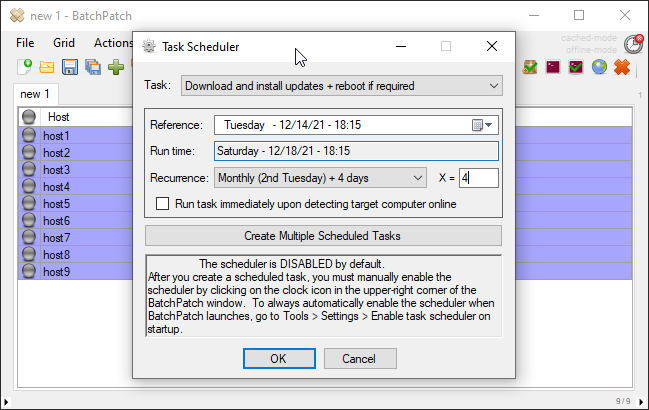
To make the task recurring, choose the desired recurrence option. If you want to have your recurring monthly Windows Update task coincide with Microsoft’s Patch Tuesday, which is the second Tuesday of the month, then you can use the Monthly (2nd Tuesday) + X days option. If your monthly maintenance window is always scheduled for the Saturday that comes after Patch Tuesday, then you can use Monthly (2nd Tuesday) + 4 days, for example.
When you have set your task to do what you want (in my example I’ve again chosen the standard Windows Update option to Download and install updates + reboot if required, you’ll need to enable the scheduler by clicking on the red clock/timer icon in the upper right corner of the BatchPatch window. It will turn green when it’s clicked on, indicating that it’s enabled.
Now, what if you want the task to be able to run even if the computer is not logged on and BatchPatch is not open and visible? For that you’ll need to enable the BatchPatch run-as-service feature. Click on Tools > Run BatchPatch as a service. You can then install the BatchPatch service, which will run always when the computer is on. Any grids that you create can then be sent to run in the service instance so that your scheduled tasks in those grids will be executed regardless of whether or not someone is actually logged on and looking at the BatchPatch console.
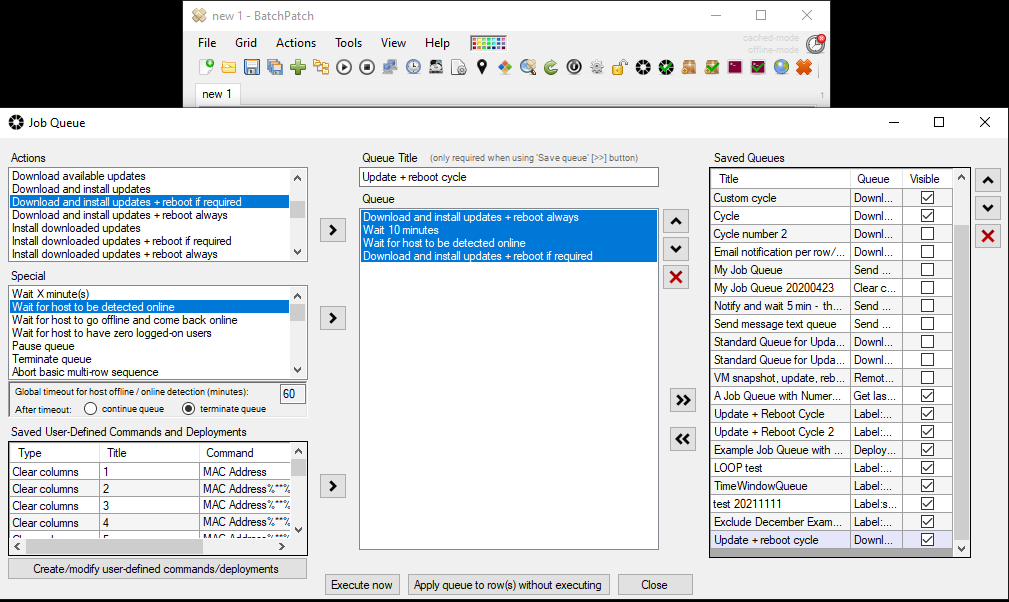
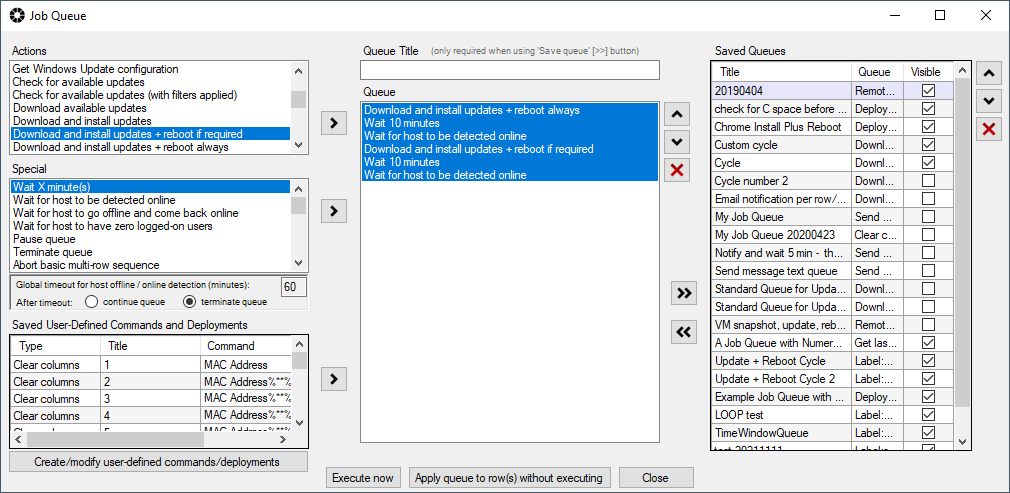
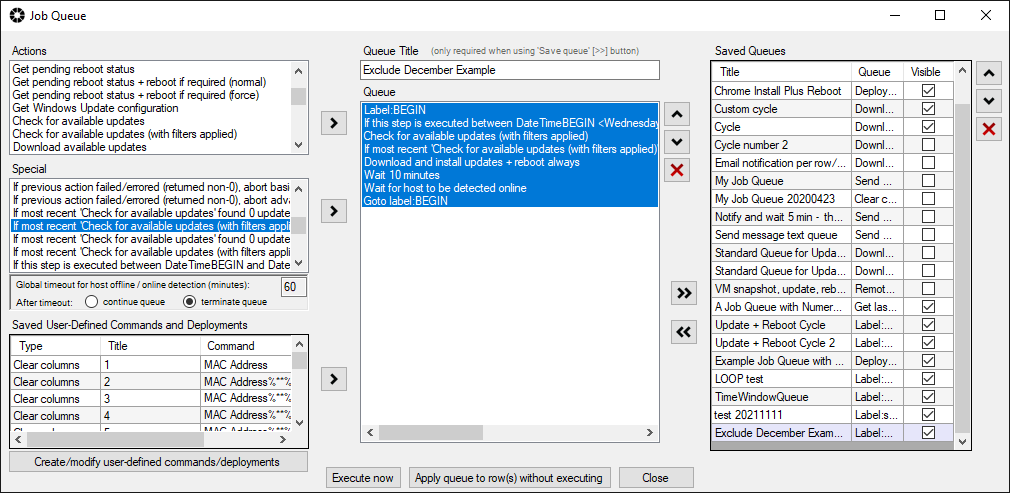
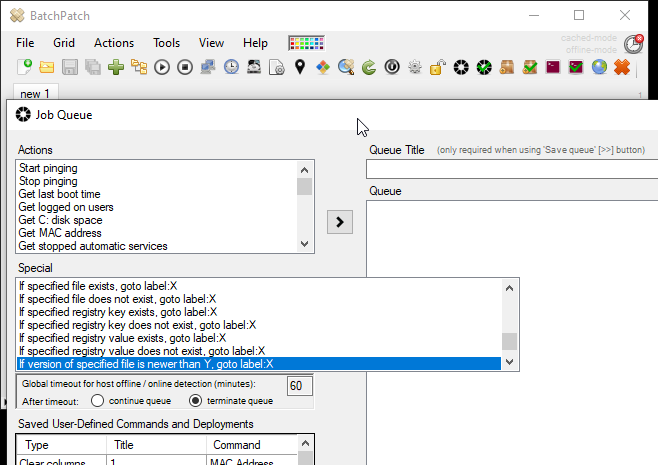
And what if you want to do more than just run a standard Windows Update download/install/reboot operation? What if you want to have that actually execute a few times to ensure that after the reboot occurs that no additional updates are waiting to be installed? (We’ve all seen times where in Windows, after you install Windows updates and reboot, all of a sudden more/new updates are available for installation. For that you can use the BatchPatch Job Queue. The job queue enables you to execute multiple actions in a row on a target computer. To launch the job queue, select your desired target hosts in the grid, and then choose Actions > Job Queue > Create/modify job queue. You can then choose a set of steps that you want each host to execute. In this case I’ve added the following steps to my job queue:
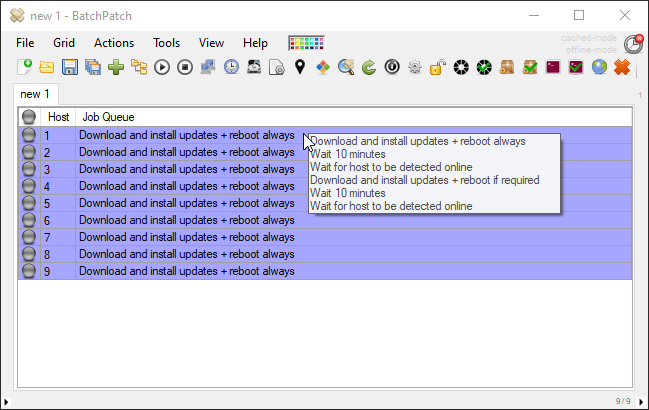
Download and install updates + reboot always Wait 10 minutes Wait for host to be detected online Download and install updates + reboot if required |
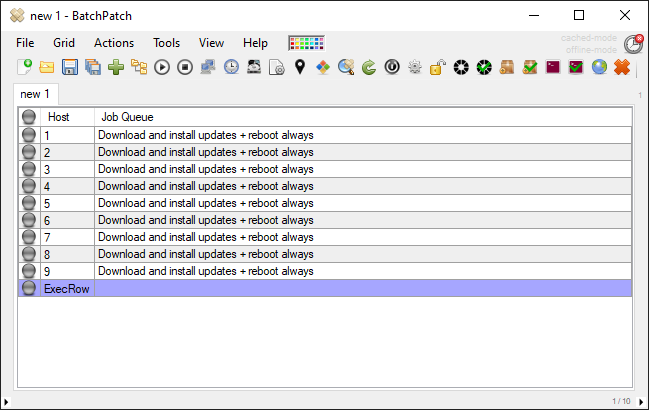
You can then save the job queue by using the double right arrow button (>>). Once it has been saved, it can be executed as a scheduled task, so you can just go back to your scheduled task window and change the drop-down menu to point to the job queue that you just created. In my case I titled the queue Update + reboot cycle, so I see it listed in the drop-down menu under “Job queue (Update + reboot cycle)”
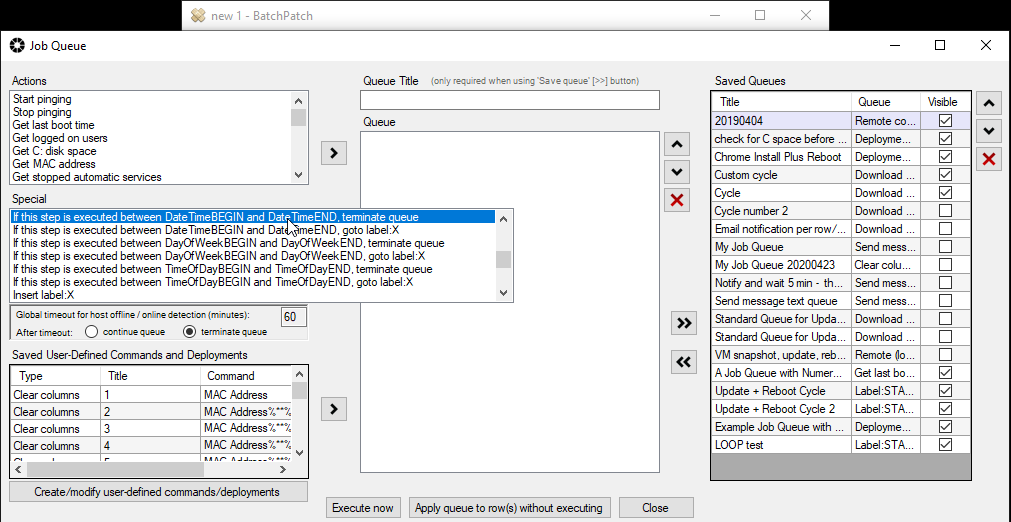
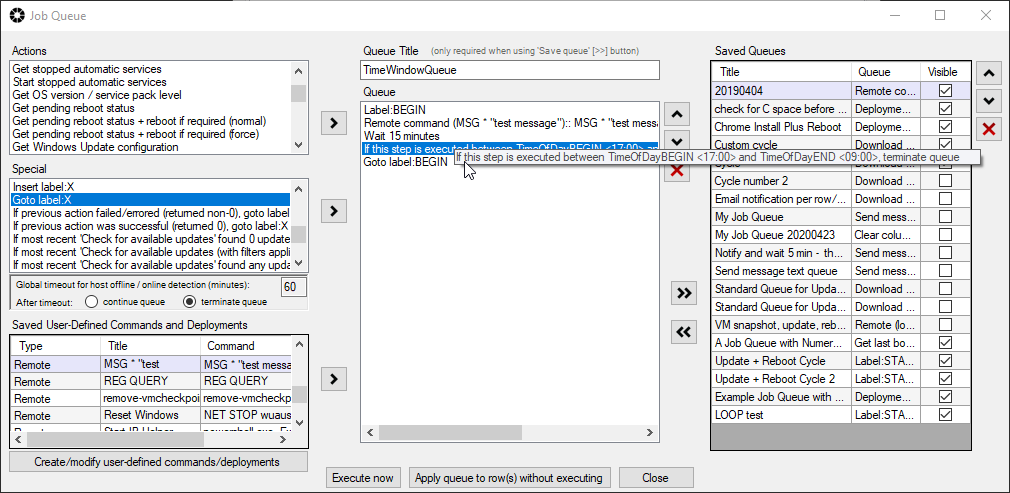
Of course the job queue can be something much more complex, if desired, because maybe you need to execute a certain script before or after the Windows Update process, or perhaps you need to perform a software deployment, or maybe something else altogether. Nearly anything you can think of can probably be included in the job queue, and it can also do branching and looping, or terminate based on specified conditions. There are lots of options.
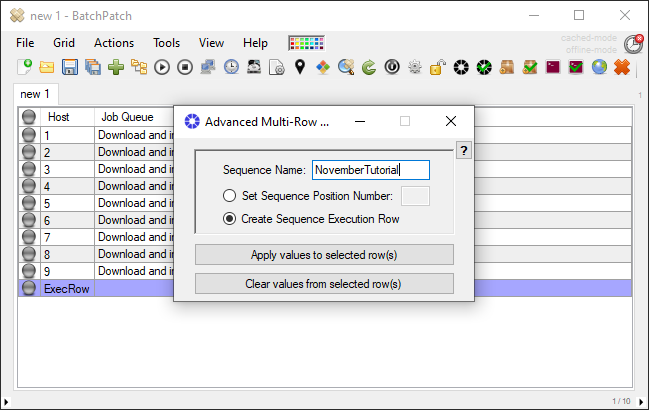
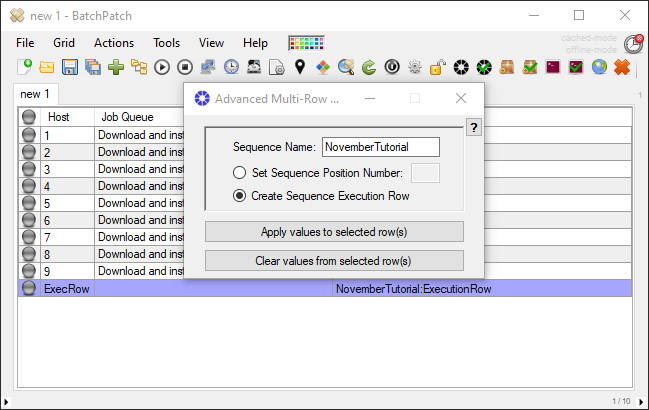
What if you want to orchestrate an entire sequence where numerous computers are involved, but where maybe certain computers execute certain tasks, other computers execute various other tasks, and there are uptime/downtime dependencies such that some computers have to be online while other computers are offline. Maybe, for example, you can only have a single computer be offline at any given time in a sequence that involves numerous computers, and you need to be able to trigger the Windows update and reboot process on all machines, in an automated fashion? You can use the Advanced Multi-Row Queue Sequence for that. Check out some tutorials here:
Orchestrating Complex Update And Reboot Sequences Involving Multiple Target Computers