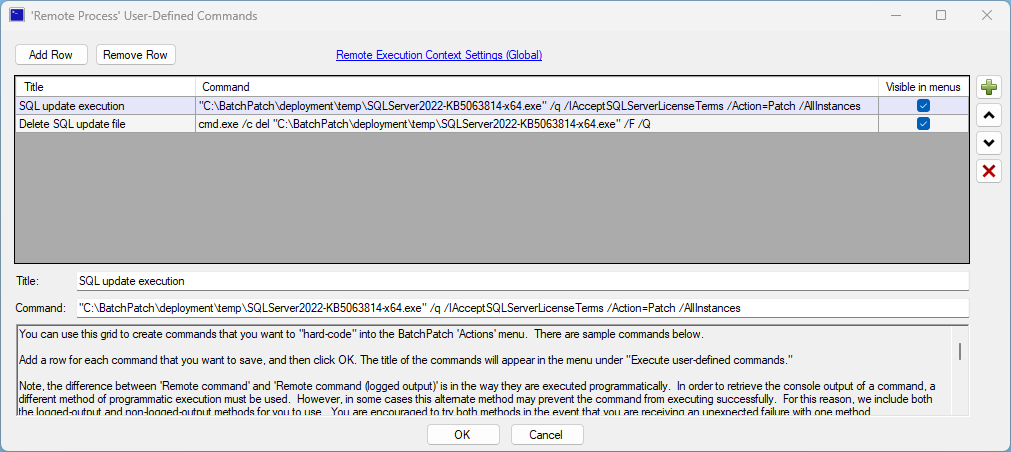
We have received some reports that using BatchPatch offline mode to install the most recent monthly cumulative update for Windows 11 is now failing with the following errors appearing in the Remote Agent Log column in the grid (this log can also be accessed by using Actions > Windows updates > View BatchPatch.log or by opening the BatchPatch.log file directly on the target computer in the remote working directory, which is defined in BatchPatch Tools > Settings > Remote Execution > Remote working directory). The default location is C:\Program Files\BatchPatch\BatchPatch.log
The error that appears in the log is:
Copy To Cache: Failed. HRESULT: -2145095681
We have also observed this other error, though much less frequently:
Copy To Cache: Failed. HRESULT: -2146467818
We are experiencing the problem on our systems too. Microsoft has (once again) made changes to the way that Windows Update functions, which is now causing this feature in BatchPatch to not work.
The current release of BatchPatch (version 20250821) has an option under Tools > Settings > Windows Update > Automatically apply offline mode workaround for CopyToCache failure (beta) that you can use to automatically employ the workaround described below.
However, for those of you with older versions, I will illustrate below how to effectively work around this issue.
Identifying the Issue:
The relevant line in the Remote Agent Log for the target system is:
skipped> 2025-03 Cumulative Update for Windows 11 Version 24H2 for x64-based Systems (KB5053598) - Reason: Update not downloaded/cached |
And here is a screenshot of the Remote Agent Log column in my BatchPatch instance where I’m seeing this error right now. Notice that in the section that starts with Begin copying files to Windows Update cache, the first update (2025-03 Cumulative Update for Windows 11 Version 24H2 for x64-based Systems (KB5053598)) contains 16 files. Each file’s line in the log shows Copy To Cache: Failed. HRESULT: -2145095681 at the end:
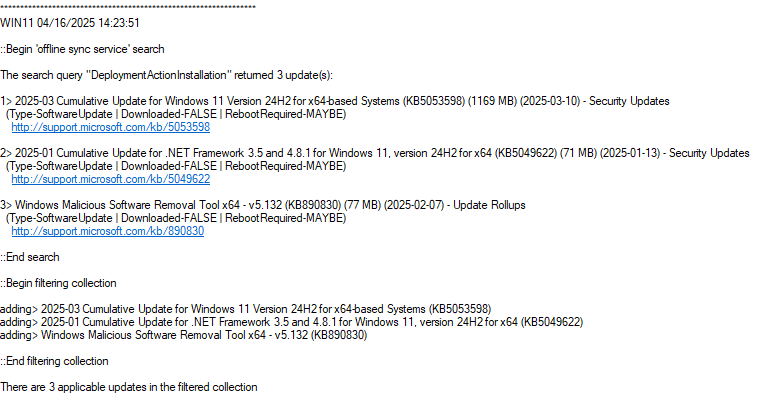
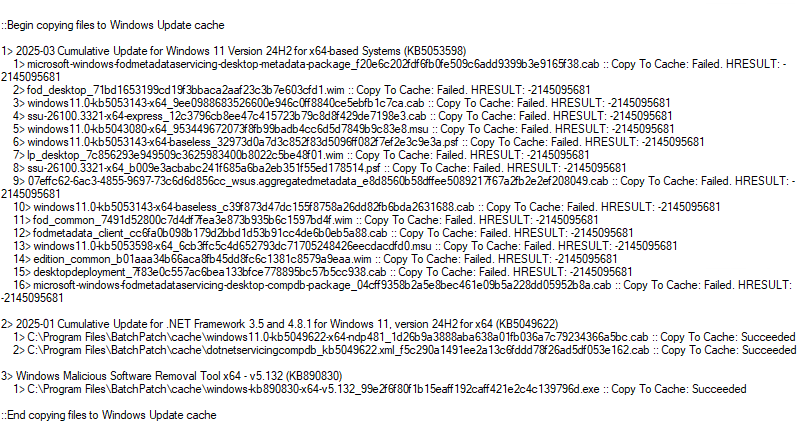
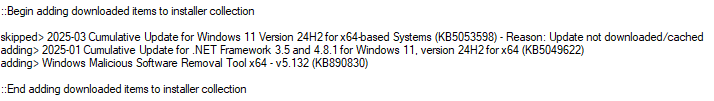
We can see that the KB5053598 2025-03 Cumulative Update was skipped (because it wasn’t able to be cached even though the update files were successfully downloaded). The other two updates (KB5049622, KB890830) still installed successfully. To install the skipped cumulative update, I’ll first examine the list of files that the update contains. If we look at the list of files that the 2025-03 cumulative update contains, we can see there are two files with .MSU extension.
5> windows11.0-kb5043080-x64_953449672073f8fb99badb4cc6d5d7849b9c83e8.msu :: Copy To Cache: Failed. HRESULT: -2145095681 |
13> windows11.0-kb5053598-x64_6cb3ffc5c4d652793dc71705248426eecdacdfd0.msu :: Copy To Cache: Failed. HRESULT: -2145095681 |
We can deploy these files directly to the target computer(s) using the BatchPatch Deploy feature. The 2025-03 Cumulative Update is KB5053598, so I’m actually going to start with the other KB5043080. In this case I’m pretty confident that KB5043080 isn’t applicable to the computer, but I want to see what happens when I try to install it. It’s probably there as a prerequisite for machines that do not already have the update installed. Even though I expect KB5043080 won’t install due to not being applicable, I want to be thorough and make sure that I attempt to install any .MSU file that is contained in KB5053598. It will not always be sufficient to *only* install the KB5043080 (or whichever KB ID matches the current month’s cumulative update KB ID). If the cumulative update contains other child .MSU files in addition to the primary .MSU for the KB ID of the parent update, we should generally always attempt to install those other child updates first in order to be sure that any prerequisites are met before we attempt to install the .MSU for the KB ID of the parent update, which in this case is KB5053598 — the March 2025 monthly cumulative update.
Workaround: Deploying the .MSU Update Files Directly with BatchPatch
The current release of BatchPatch (version 20250821) has an option under Tools > Settings > Windows Update > Automatically apply offline mode workaround for CopyToCache failure (beta) that you can use to automatically employ the workaround described below.
However, if you have an earlier version of BatchPatch, below I will illustrate below how to effectively work around this issue:
During the offline cached mode Windows Update process, the cumulative update is downloaded to the BatchPatch local cache directory as a bundle of files. When this issue first cropped up, one of the key changes that Microsoft made was to begin delivering the .MSU version of the update file included in the bundle of files for the cumulative update. So now if you experience the error and failure that is described by the title of this article/posting during the offline cached mode installation process, you can still get the update deployed with the BatchPatch Deploy method, by directly deploying the .MSU file(s) from the BatchPatch local cache directory to your target computers. This process is explained below.
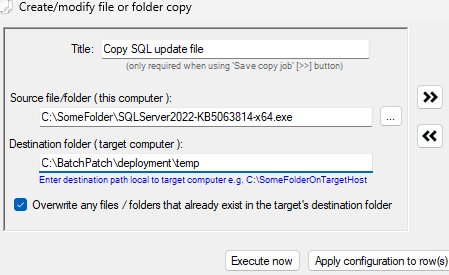
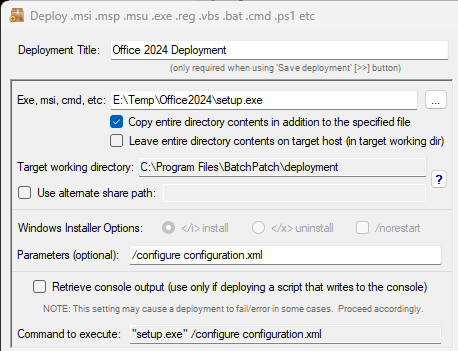
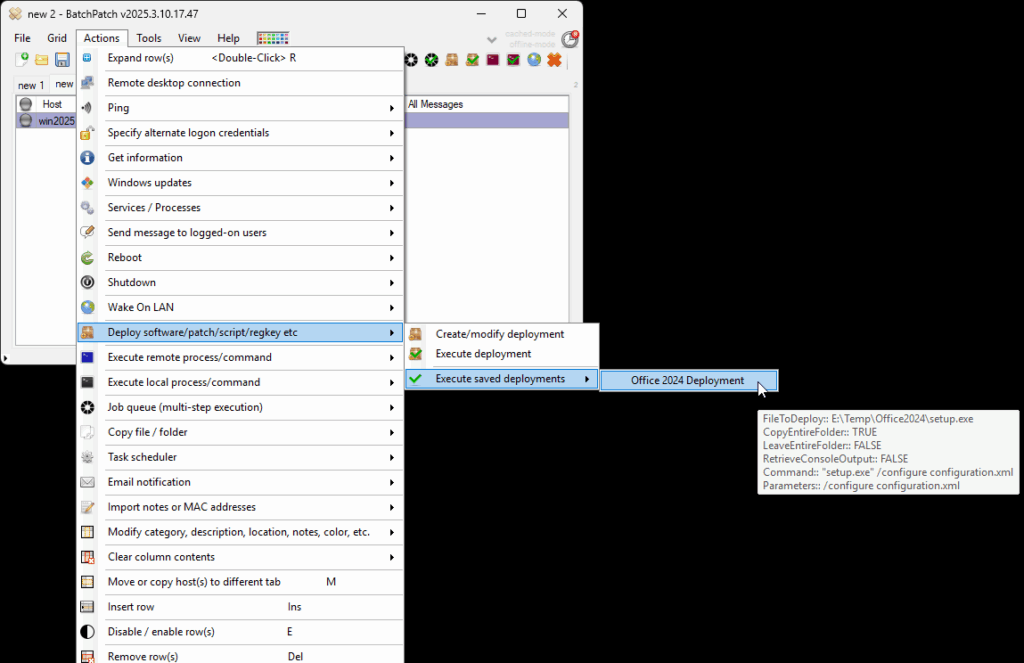
- With the desired target host selected/highlighted in the grid, I click on Actions > Deploy > Create/modify deployment.
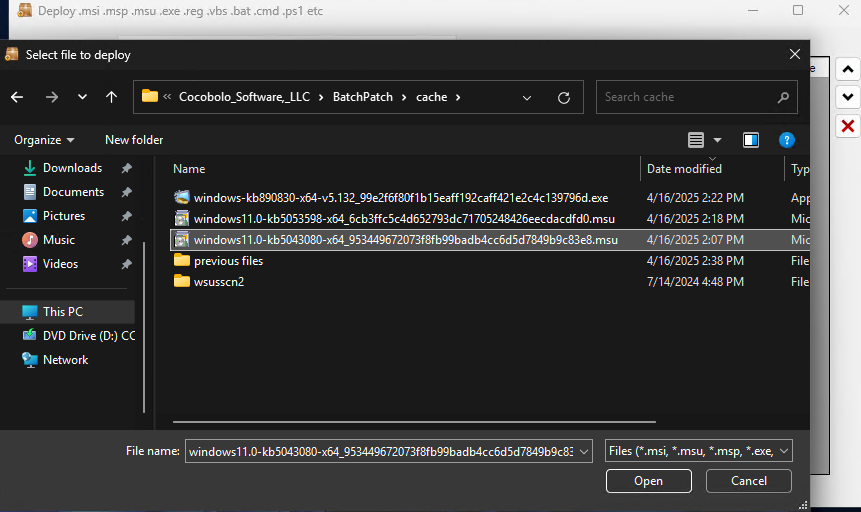
- Next I click on the … file browser button to select the .MSU file deploy. I browse to the BatchPatch cache directory on my BatchPatch computer (this location is defined under Tools > Settings > Windows Update > Local update cache directory), and then I select the .MSU file that I want to deploy. The first file I want to deploy (or attempt to deploy) is the KB5043080 .MSU file.
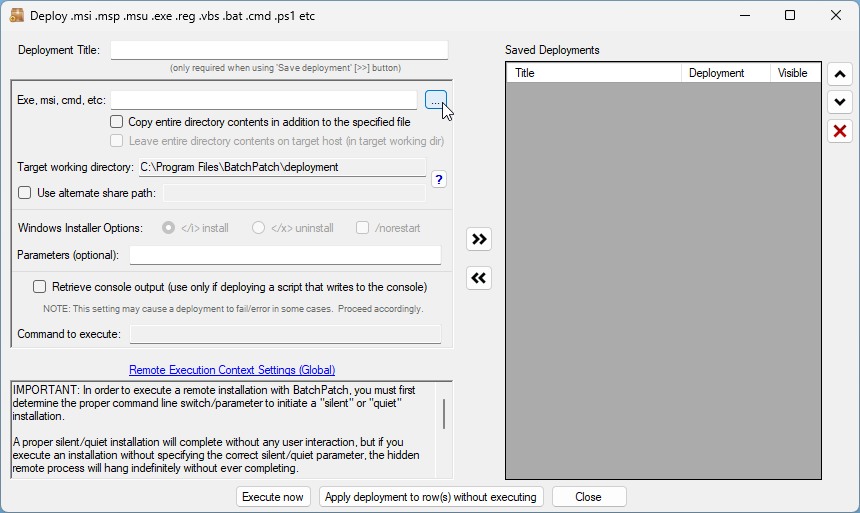
- In this case I’m going to choose the option for a singular .MSU deployment:
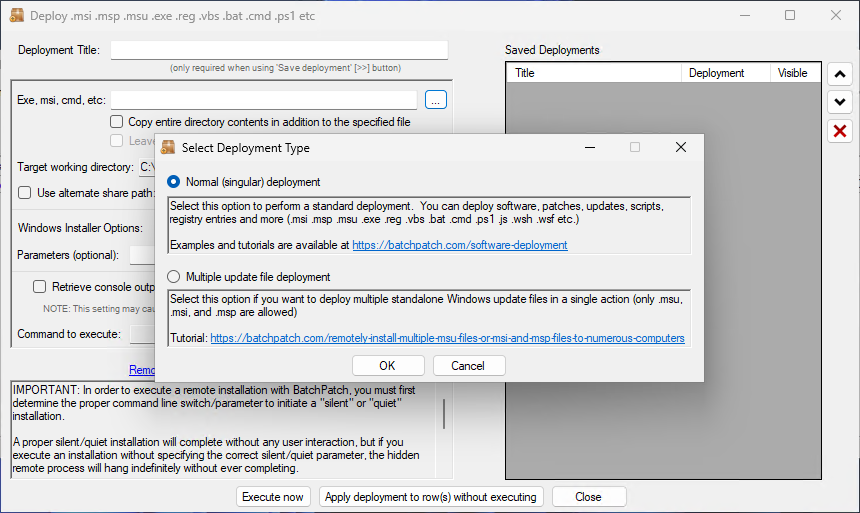
- I browse to location of the desired .MSU file, and choose it.
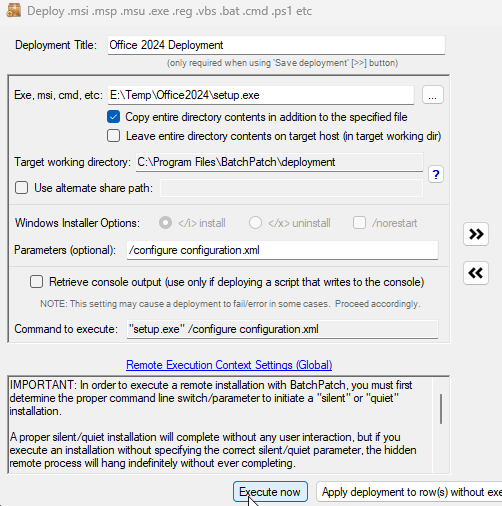
- I chose to select the /norestart option so that the installer does not reboot the target computer when it finishes installing the update.
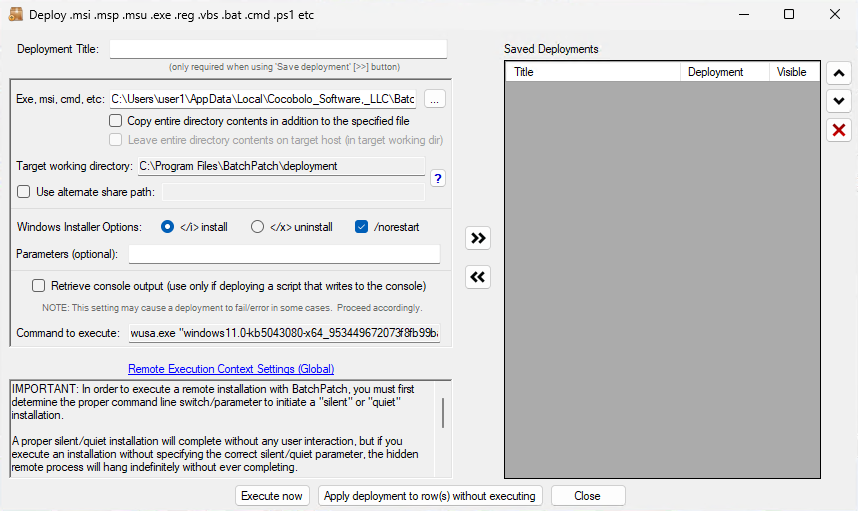
- Finally I’ll click Execute now to begin the deployment process. This will tell BatchPatch to copy the file to the target computer and then initiate its installation.
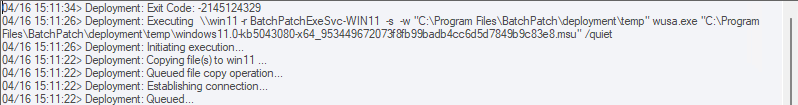
- As I suspected, this update is not applicable to the system. I know this because the deployment completed with the All Messages log column showing Exit Code: -2145124329, which means Update Not Applicable. In the next version of BatchPatch we’ll make sure that Update Not Applicable is included in the log right next to the exit code so that there is no confusion. However, in the current version of BatchPatch you’ll only see the HRESULT exit code value.
- Now I’ll follow the exact same process to deploy the .MSU for KB5053598.
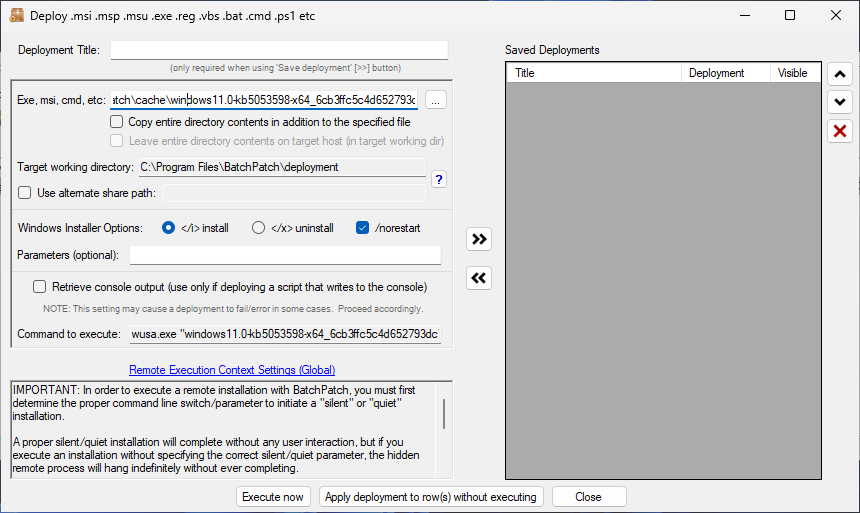
- When this one finishes, I see Deployment: Exit Code: 3010 (SUCCESS – REBOOT_REQUIRED)
- I can now initiate the reboot in BatchPatch. If I had NOT selected the /noreboot switch in the deployment configuration, the target computer would have rebooted itself immediately after completing the update installation. However, I prefer to have BatchPatch initiate and monitor the reboot, rather than the target computer rebooting itself.