Forum Replies Created
-
AuthorPosts
-
dougModerator
Great, thanks. Glad you got it worked out. I see that the ghacks link you posted above mentions some registry values that enable/disable the .NET Core updates from being available in Windows Update, so perhaps you just need to tweak those so that you can see them through Windows Update? Not sure. Worth looking at though. Take care.
dougModeratorThis is a generic failure HRESULT value. I couldn’t tell you why it’s failing, but it could be just that it needs another try. Or it could be that you’d have to reinstall .NET MVC on there, or reboot the system and try again etc.
With regard to “I guess I’ll need to hunt for the .net core patch individually” I’m not sure if I understand what you mean.
dougModeratorThe ‘Remote Agent Log’ column in BP is where you can see the details and reason for the update installation failure for the current Windows Update operation. You can view the historical log under ‘Actions > Windows Update > View BatchPatch.log’
dougModeratorUse ‘Actions > Windows updates > Opt-in to Microsoft Update (enable updates for other MS products)’ to turn on the setting for the selected target computer(s)
Then set BatchPatch server selection to use ‘Microsoft Update’ under ‘Tools > Settings > Windows Update > Server Selection > Microsoft Update’
.NET, in general, is normally considered part of Windows and typically does not require the setting to be enabled. It’s interesting that they would treat .NET Core differently. Kinda makes sense, but kinda doesn’t. Oh well. Good to know either way. Thanks.
dougModeratorYou’re finding optional, “seeker” updates. In Windows 10/2019 build 1809 or newer, if you go to the Windows Update control panel on a machine that was recently updated, you may find additional optional updates available if you use the ‘Check for updates’ button. Microsoft releases these optional updates usually toward the end of the month. Microsoft says that while the updates do not contain any new functionality, they may contain fixes for specific outstanding issues. They are released through what is essentially a completely separate channel that is only available to “seekers” who use the ‘Check for updates’ button. At the time they are made available to “seekers” as optional updates they are not yet released to WSUS nor are they released to the normal automatic updates channel in ‘Windows Update’ or ‘Microsoft Update.’ However, Microsoft generally moves them from optional status into the normal release channel in the following month after they are initially released to only “seekers” who manually use the ‘Check for updates’ button in the Windows Update control panel.
In BatchPatch you can find these optional updates by selecting the checkbox under ‘Tools > Settings > Windows Update > Search for only optional software updates’
Unless you have a specific need for one of these optional updates, we generally do not recommend installing them. We believe that unless you have a specific need for a fix that is included in one of these updates, it usually makes the most sense to wait until the following month when Microsoft moves them from optional status to the normal deployment channels.
March 25, 2021 at 2:58 pm in reply to: Feature Request: Get List of Installed Programs: DisplayVersion #12801dougModeratorThank you for the suggestion. We’ll consider this for a future build.
dougModeratorThey released PsExec v2.33 yesterday (March 23, 2021). We believe the issue is now properly resolved in this version.
Thanks.
dougModeratorThey released PsExec v2.33 yesterday (March 23, 2021). We believe the issue is now properly resolved in this version.
Thanks.
dougModeratorIf you don’t see it then yes you should download the latest version. Use ‘Help > Check for updates’ in the app. The default behavior of the app is to notify you of any available update each time you launch the app, but maybe you disabled that.
dougModeratorSee the column that says “Visible” with all of the checkboxes…
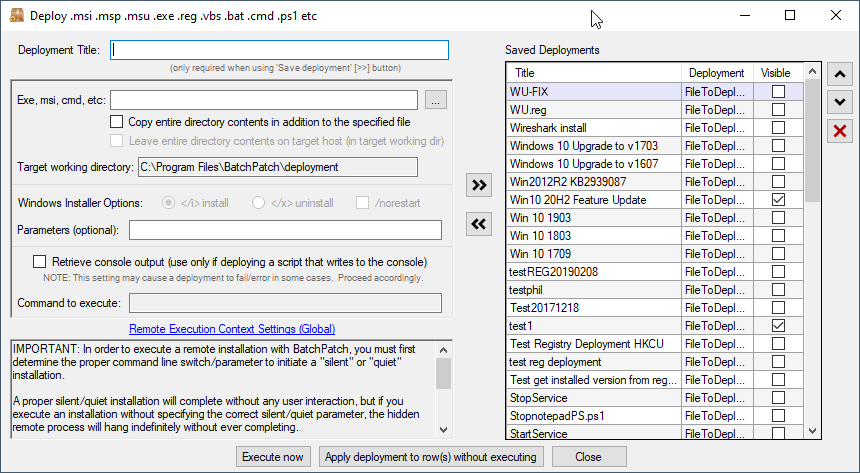
We’ll consider additional organization options for a future version
dougModeratorThey’re all sortable by name already. I’m not sure what you’re doing. For example, go to ‘Actions > Deploy > Create modify’ and in the ‘Saved Deployments’ grid on the right side of the window you can organize your commands by sorting them and/or by making them either visible or invisible in the BatchPatch action menus.
dougModeratorYes. If you select “Include Upgrades” to install a feature update, then BatchPatch will not be able to install any “regular” updates until you de-select the “Include Upgrades” box and re-select the other classifications. For the other classifications we generally recommend selecting the entire left-hand column of classifications:
Critical
Security
Definition
Updates
Update RollupsdougModeratorCorrect. If you leave it set to “Search for only optional software updates” then moving forward it’s not going to find any regular updates and will only find optional updates, which generally we do not recommend installing except in cases where you specifically need one like you did in this particular instance.
March 16, 2021 at 8:34 pm in reply to: stopping service exits with “System error 5 has occurred. Access is denied.” #12782dougModeratorExcellent. You’re welcome.
March 16, 2021 at 5:47 pm in reply to: stopping service exits with “System error 5 has occurred. Access is denied.” #12780dougModeratorGo to ‘Tools > Settings > Remote Execution’ and uncheck the ‘Interactive’ boxes. That should do it. Please let me know if it resolves the issue.
Thanks.
dougModeratorIt looks like this is being delivered as an “optional update” through the normal Windows Update and Microsoft Update channels. This means that in addition to deploying the KB directly as a standalone .MSU file using the instructions at the link you posted above (using the standard BatchPatch deployment method), you can also use the normal Windows Update actions in BatchPatch to deploy this, but you’ll have to first go to ‘Tools > Settings > Windows Update’ and check the box for “Search for only optional software updates”
dougModeratorIt appears that the current version 2.32 doesn’t actually fix the root issue, so while the original PoC for the LPE doesn’t work on 2.32, the researcher who found the issue was able to quickly modify his PoC to work on 2.32. That said, we believe Microsoft is now working on another update, so it might make sense to wait for that to be released, but of course this is up to you. As an alternative you could also use PaExec if you want. With PaExec, if you specify alternate credentials (not an issue when using integrated security), it obfuscates but does not encrypt them when sending them across the network. While this is not optimal, it’s also not necessarily a deal-breaker, but there’s a tradeoff to consider. You can read more on that tradeoff here: https://batchpatch.com/psexec-v2-1-all-network-communication-is-now-encrypted
As for updating… You can just replace the psexec.exe on your computer with the new one (though you should keep a backup of the old one too in case you want to revert to it). Or you can use ‘Tools > Settings > Remote Execution > Use psexec.exe custom filepath’ to point BatchPatch to any version of PsExec or PaExec you want.
dougModeratorI don’t know how you have “downloaded and staged the install” …
However, I can tell you that BatchPatch can apply feature updates in two different ways, either by using the built-in Windows Update actions (make sure the update classification ‘Upgrades’ is checked under ‘Tools > Settings > Windows Update), or by using a deployment with the ISO media:
dougModeratorPlease contact us at https://batchpatch.com/contact
dougModeratorYou can enable sorting under ‘Tools > Settings > Grid preferences > Enable row sorting’
dougModeratorHello – First, in case you didn’t see these, here are some links that demonstrate how to send email notifications in a few different ways:
https://batchpatch.com/how-to-send-email-notifications-in-batchpatch
https://batchpatch.com/using-email-notifications-to-check-status-of-automated-patching-events
With regard to your question, I’m actually not quite sure I understand what you mean. A row is not a part of a job queue. Rather a job queue can be saved in the global saved job queues list and then later executed for a row in a grid… OR a job queue can be directly applied to a row in a grid and be saved there instead of (or in addition to) the global saved job queues list. Maybe you applied a job queue directly to a row? And you’re asking how to undo that or clear the job queue from that row? One method is to go back to the job queue window and just apply a new queue to the row and overwrite the old one. It can be another queue or an empty queue. Another option is to clear the job queue contents from the row using ‘Actions > Clear column contents’ for the desired row.
dougModeratorVery intersting! Thanks for the update. I’m glad you got it working. I don’t have any good ideas for why the original method would have stopped working. It’s particularly strange that it would stop working with a 2250 exit code and yet the run-as method works properly. Doesn’t make a lot of sense, but glad you have a solution/workaround.
dougModeratorThe “update reboot cycle” was really just a limited BatchPatch job queue. It was deprecated for years and finally removed in version 20200924. You can get identical functionality plus a lot more customization options in the BatchPatch job queue.
Tutorial: https://batchpatch.com/update-reboot-cycle-with-the-batchpatch-job-queue
February 20, 2021 at 2:31 pm in reply to: Start Stopped Automatic Services. Does Not work on 2021.1.29.12 #12755dougModeratorThe command runs under “Remote process/command (logged output)” not “Remote process/command”, so that’s expected/good. I just wasn’t certain if you were using that command for every try, so I wanted to cover all possibilities just to be safe. I would suggest leaving “Remote process/command (logged output)” set to ‘Elevated token’, and you should be good to go.
Thanks.
February 20, 2021 at 11:58 am in reply to: Start Stopped Automatic Services. Does Not work on 2021.1.29.12 #12753dougModeratorPlease look at ‘Tools > Settings > Remote Execution > Remote Execution Context’
Try the following ‘Remote Execution Context’ settings for ‘Remote process/command’ and ‘Remote process/command (logged output)’
SYSTEM
SYSTEM + interactive
Elevated token
Elevated token + interactiveDo any of the 4 options work?
dougModeratorGood, I’m glad that worked.
It’s good/fine to leave it that way. Actually ‘SYSTEM’ without interactive, is the default setting in the most recent version of BP for ‘Deployment’ because as of today, we think this is probably the most compatible option for deployments, in general. However, it’s possible that you could encounter a deployment in the future which requires ‘Elevated token’ instead.
dougModeratorExcellent. Glad you got it worked out. Thanks for explaining what the issue was. This is helpful. Essentially the issue is that when “force IPv4” is enabled BP has to do an explicit DNS lookup, otherwise it can end up pinging the IPv6 address (if IPv6 is enabled). However, when entering an IP address directly into BP as a hostname, obviously that should always be able to work regardless of the “force IPv4” setting, and a DNS lookup should not be required, so I think we can make an adjustment to the code that will take care of that. Presumably the problem in your case was specifically tied to the stale PTR record. My guess is that *just* having the stale A record wouldn’t have caused the issue. Regardless, I think we can make an adjustment to the code to at least ensure that an IP that is input directly into BP will never do the lookup.
dougModeratorWhen you unchecked it… did it ping the IPv6 address or still IPv4 address?
dougModeratorAlso… see what happens if you toggle the setting ‘Tools > Settings > General > Force pinger to always use only IPv4’
dougModeratorIt’s really unclear to me how or why this could happen. I can only make the same suggestions that I made above… (you didn’t mention if you tried any/all of them) … with one addition:
*reboot the BP computer
*re-add the target computer to BP from scratch in a new row
*add the target computer by IP instead of name
*add the target computer by FQDN instead of short name or IP
*check to see how many network adapters are on the computer. if there are multiple adapters, disable any adapters that are not currently in usePlease report back and let me know if any of these does the trick. While I don’t have any other suggestions to make at the moment, it will be helpful for us to know if any of these things works.
-
AuthorPosts
