First, let me just say that PsExec is *NOT* malware and it’s *NOT* a virus. It’s simply a very useful tool, particularly for systems administrators. However, because of the fact that it is so useful to sysadmins, it also happens to be useful to hackers. Some of the major anti-virus software vendors have at one point or another ended up flagging PsExec as malware or unsafe software. In some cases this is because of unsophisticated malware/virus detection, and in other cases it’s simply due to the fact that PsExec is sometimes used by malicious hackers, so some vendors and organizations think that by identifying instances of PsExec they could potentially be identifying hacker/attacker activity. However, just because someone could use PsExec maliciously does not mean that all uses of PsExec are malicious. Remember, it’s just a useful tool. Furthermore, and perhaps most importantly, in order for PsExec to be used maliciously, the attacker would need to have administrator credentials for the target system. And if an attacker is already in your network and has already obtained administrator credentials for a target system, then you can be sure that the attacker will *NOT* need PsExec to compromise the machine.
PsExec has been painted in a bad light and even banned in some organizations simply due to the fact that attackers sometimes make use of it. However, banning it does not actually make a network any safer. It merely enables a box on a security checklist in a bureaucratic environment to be checked/ticked. This may even create a false sense of security since it doesn’t actually increase the network’s security in any meaningful way.
If your anti-virus software has been configured to block PsExec through some type of execution policy, here are your options for getting it working again:
- Perhaps the most obvious method would be to modify the execution policy so that it no longer blocks PsExec. 🙂
- Another option, if your AV software has such functionality, is to whitelist PsExec. In this case you should whitelist psexec.exe as well as psexesvc.exe
- The simplest method to prevent your antivirus software from blocking PsExec is actually using a built-in switch that PsExec offers to change the remote service name. This option exists in PsExec version 2+. This method works for the large majority of situations, but depending on the actual blocking mechanism that has been used in your environment, it’s possible that this method might not work for you.
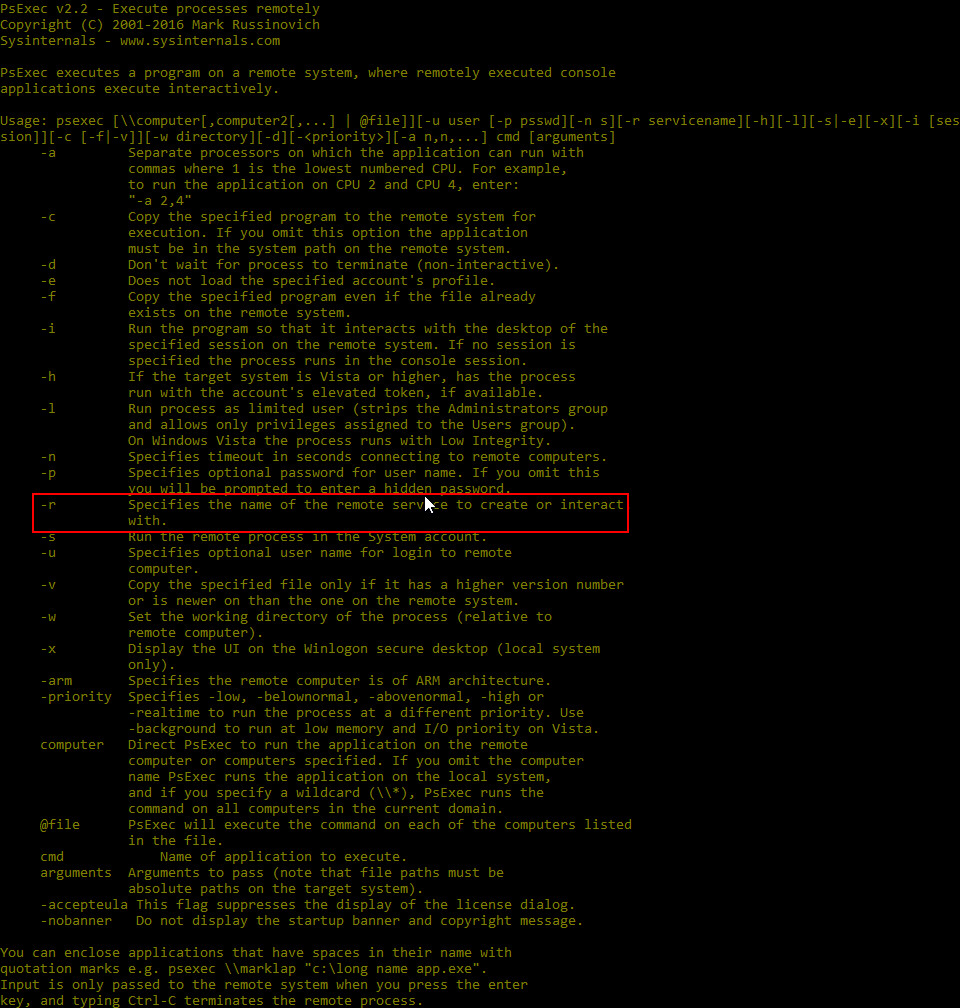
-r Specifies the name of the remote service to create or interact with
Under normal circumstances when PsExec.exe is executed on computer A, it creates a connection to a target computer B. On computer B a new service is created called PSEXESVC with an executable file psexesvc.exe. When you use the -r switch you are able to specify a new/different service name to be used, so the target computer will create a service and associated executable with the name you specific rather than the default/generic psexesvc. Believe it or not, this is actually enough to bypass or prevent detection in many/most cases, though again I would note that it really depends on the actual blocking mechanism that’s in place in your environment.
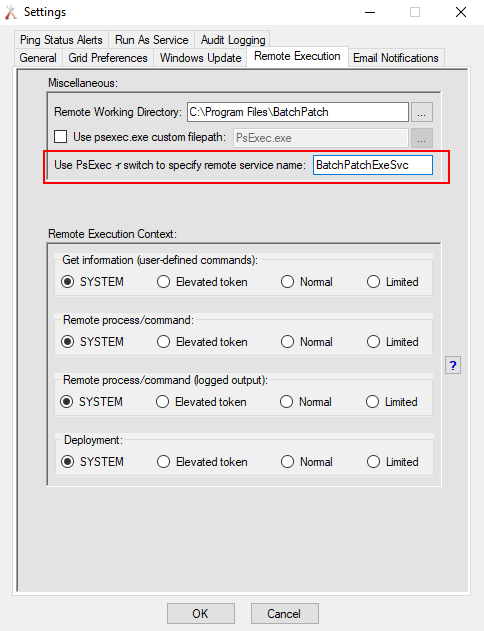
This switch can be utilized when working with PsExec directly at the command line on a particular computer or it can also be used inside of BatchPatch. In BatchPatch go to ‘Tools > Settings > Remote Execution’. You’ll need to modify the value next to ‘Use PsExec -r switch to specify remote service name’. You can use any name that you want here. BatchPatchExeSvc is not a bad choice, and it’s what I have specified in my instance of BatchPatch, as you can see in the screenshot below. EDIT 2021: We actually made this the default configuration in BatchPatch
Normally it’s just the remote service PSEXESVC and/or psexesvc.exe that is blocked by an execution policy, but if you want you could go a step further and actually provide a new name for the PsExec.exe too. This file normally only would exist on the BatchPatch computer. You can change its name to whatever you want such as YourCustomName.exe and then in BatchPatch modify the value for ‘Use psexec.exe custom filepath:‘ which also lives under Tools > Settings > Remote Execution. You’ll need to specify the full filepath to your newly named .exe file, so for example C:\YourDesiredPath\YourCustomName.exe